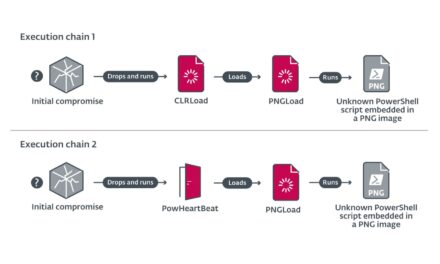
If there was a hack, then there was a hacker – cyber threat analysis is a detective’s job, like an Agatha Christie novel. See how Check Point Research unravels cyber mysteries, what clues they look for and what tools they use to solve cases such as “Cyber on the Orient Express” and “Eye on the Nile”.
Related Posts
Voters-draw/RCA-Sponsors
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
Slide
CybersecAsia Voting Placement
Gamification listing or Participate Now
|
PARTICIPATE NOW |
|
|
Vote Now -Placement(Google Ads)
Top-Sidebar-banner
Whitepapers

Closing the Gap in Email Security:How To Stop The 7 Most SinisterAI-Powered Phishing Threats
Insider threats continue to be a major cybersecurity risk in 2024. Explore more insights on …Download Whitepaper
2024 Insider Threat Report: Trends, Challenges, and Solutions
Insider threats continue to be a major cybersecurity risk in 2024. Explore more insights on …Download Whitepaper
AI-Powered Cyber Ops: Redefining Cloud Security for 2025
The future of cybersecurity is a perfect storm: AI-driven attacks, cloud expansion, and the convergence …Download Whitepaper
Data Management in the Age of Cloud and AI
In today’s Asia Pacific business environment, organizations are leaning on hybrid multi-cloud infrastructures and advanced …Download Whitepaper
Middle-sidebar-banner
Case Studies

India’s WazirX strengthens governance and digital asset security
Revamping its custody infrastructure using multi‑party computation tools has improved operational resilience and institutional‑grade safeguardsRead more
Bangladesh LGED modernizes communication while addressing data security concerns
To meet emerging data localization/privacy regulations, the government engineering agency deploys a secure, unified digital …Read more
What AI worries keep members of the Association of Certified Fraud Examiners sleepless?
This case study examines how many anti-fraud professionals reported feeling underprepared to counter rising AI-driven …Read more
Meeting the business resilience challenges of digital transformation
Data proves to be key to driving secure and sustainable digital transformation in Southeast Asia.Read more
Bottom sidebar
Other News
Blackpanda Japan Announces Strategic Partnership with SoftBank to Strengthen Cyber Incident Response in Japan
SINGAPORE, Feb. 10, 2026 /PRNewswire/ …Read More »Cohesity Collaborates with Google Cloud to Deliver Secure Sandbox Capabilities and Comprehensive Threat Insights Designed to Eliminate Hidden Malware
Embedded Google Threat Intelligence capabilities, …Read More »Shield AI, Republic of Singapore Air Force, and Defence Science and Technology Agency Expand Partnership to Progressively Field Autonomy Capabilities
SINGAPORE, Feb. 5, 2026 /PRNewswire/ …Read More »ICAC Commissioner attends APEC anti-corruption meetings in Guangzhou to foster collaborations in the Asia Pacific region
HONG KONG, Feb. 4, 2026 …Read More »VIVOTEK Enhances VORTEX with Generative AI and Safety Detection
Expanding the cloud security ecosystem …Read More »