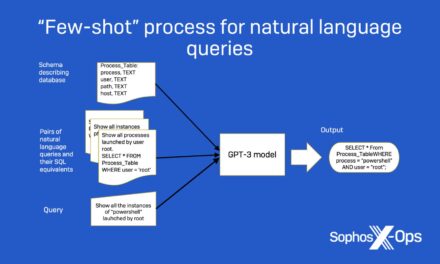
Not using DevSecOps or mandating formal sign-offs before apps are pushed into production, can leave an open door for supply-chain attacks.
Over the course of the pandemic, some of the biggest disruptions the world faced were due to attacks on critical national infrastructure, specifically supply chains.
Border and port closures, mandated work-from-home policies, and severe shortages of essential products including PPE and pharmaceuticals, have highlighted vulnerabilities in production, supply, and logistics.
More recently, a supply-chain ransomware attack against enterprise IT firm Kaseya caused a knock-on effect across more than 1,000 organizations. Security agencies globally warned customers to shut down servers after the weekend’s cyber-attack on Kaseya’s VSA product.
Was this response fast enough? What else should organizations be doing to protect their IT and OT systems and data?
Avoiding sledgehammer reactions
Regrettably, supply chain-based attacks are incredibly hard for customers to defend against. Shutting down the affected servers is a sledgehammer approach. While the intent is good, it will not prevent these types of attacks from determined adversaries.
New findings in PaaS & IaaS Security research have underlined how the Cloud has changed everything we know about security; 100% of the companies surveyed had experienced a security incident but continued to expand their cloud service footprint.
The expansion of cloud services has naturally led to increased complexity and risk, accompanied by the discovery of some startling security blind spots. These include 30% of respondents not mandating formal sign-off before pushing to production, and 40% of respondents not having a DevSecOps workflow.
Identifying IT/OT security blind spots
A truly strong security strategy that covers both endpoint and network is needed to help identify when assets are compromised in a supply chain attack but also give organizations forward notice before they occur.
Part of that strategy includes assuming you are going to get breached, but ensuring you have the right tools and support in place so an attack can be contained.
With the risk of harm obviously no longer limited to sprawling enterprises with huge budgets, the incident should trigger new security discussions in more IT departments across the Asia Pacific region.
To improve supply chain cyber defenses, here are the top three best practices:
- Reduce the risk of cloud services being exploited: use an AI-driven threat detection and response solution
- Monitor access of the deployment and its configuration
- Review and remove admin-level roles that are no longer used and/or needed
Over the next few years, we can expect to see threats to supply chain and other critical national infrastructure across a number of scenarios.
For instance, healthcare systems remain vulnerable, and continued demand for remote-working will increase attack surfaces.
Each site or situation is unique and visibility and agility are the building blocks of effective incident response. Industry and enterprise security teams must adopt an assumed-compromised mindset and focus on early, automated detections with context to enable cyber defenders to make fast and informed decisions.