Psychologists say you are not as smart as you think, and hackers know just the toxin to smear on their clickbait!
Targeting people instead of systems is the fastest and most results-driven method of hacking. The reason for this is due to the Dunning-Kruger effect, a cognitive bias where people overestimate their knowledge or ability in a certain area.
In the case of network security, people overestimate their ability to gauge risky behavior online. And why not? There is an entire adult generation in the workforce that has never known life without the Internet. They have been simultaneously consuming and curating digital content since childhood.
In 2020, we are all confident in our cyber-proficiency in this globally-connected world. Yet, the hacking continues. We have become desensitized to people and organizations announcing that their accounts and data centers have been compromised.
The psychology of phishing
We need to understand how social engineering, and by extension (spear) phishing, works, and we need to understand why we fall prey to these types of attacks.
Usually, the simple act of receiving an email and writing a response is no more exhilarating than cleaning the bathroom. On rare occasions, we get an email that genuinely gets our heart-rates up and invokes any of the six basic emotions: anger, disgust, fear, happiness, sadness, and surprise.
Hence, the social engineer’s goal is to create emotion in the target that causes irrational thought, because emotional people make mistakes. Hackers also prey on the target’s vanity in deeming oneself incapable of falling victim to hackers.
Now use a surefire trigger for strong emotional response. It depends on the individual, but the odds of an emotional response to pandemic current affairs are quite high, according to a recent survey.
Normally, it takes time in order to find a trigger that instils urgency. But the pandemic is a global health threat fitting that bill for hackers. We are all eager to keep on top of the worldwide chaos and confusion.
Anatomy of COVID-19 clickbait
So let us now look at a typical attack strategy hinging on the pandemic fears. Since finding factual information about COVID-19 has been a challenge due to so much contradictory information, ‘expert’ opinions and political bickering, this situational uncertainty is the perfect click-bait.
One URL that my company’s security research team has seen in the wild in an attempt to trick people:
hxxps:[//]cdc.gov.coronavirus.secure.server[.]shorttermrental[.]org[/]vaccine/auth/cgi-bin/cgi-bin.exe
(No worries, the link has been altered to prevent anyone reading this article from clicking it. The unmodified version of the link is also now defunct.)
Let us dissect that link:
- First, the subdomain is cdc.gov
- a ploy to trick the target into fully-believing this is information from the US Center for Disease Control, an authoritative source.
- a ploy to trick the target into fully-believing this is information from the US Center for Disease Control, an authoritative source.
- The next subdomain is coronavirus
- More info designed to trick targets into believing that this link contains critical information that will inform them about an emotion-provoking topic.
- More info designed to trick targets into believing that this link contains critical information that will inform them about an emotion-provoking topic.
- The next two subdomains are secure and server
- Innocuous and, potentially soothing, domains that further assist and hiding the true domain.
- Innocuous and, potentially soothing, domains that further assist and hiding the true domain.
- shorttermrental[.]org is the domain that is actually being resolved
- Note we use incorrect brackets to ensure our reader do not accidentally browse to a potentially felonious domain.
- Note we use incorrect brackets to ensure our reader do not accidentally browse to a potentially felonious domain.
- Within the directory of the link there is another keyword designed to invoke emotion: vaccine
- This evokes some powerful stuff worth exploring: Is the CDC endorsing a vaccine? Is there a cure?
- This evokes some powerful stuff worth exploring: Is the CDC endorsing a vaccine? Is there a cure?
- Next we have /auth/cgi-bin
- This is a directory for the Apache webserver that runs Common Gateway Interface scripts
- We have all seen this in URLs many times before, and, as we are all experts on using the internet and we never let parts of a URL we have seen before, intimidate us.
- We are very smart and our level of understanding is the long tail of the Dunning-Kruger effect [obvious sarcasm]
- cgi-bin.exe
- Having the malware hidden by repeating strings that look like something we have seen before, but may not understand
- This is a concept called semantic satiation, a psychological phenomenon in which repetition causes a word or phrase to temporarily lose meaning for the reader, who then perceives the content as meaningless.
- This technique is applied by the malware:
- /auth/cgi-bin/cgi-bin.exe
This entire URL was specifically crafted to invoke as much emotion as possible while hiding a link executable that downloads malware onto your computer. In reality, cgi-bin.exe is really the malware Win.Worm.Brontok-88 which copies itself into various folders and modifies the operating system security settings and the HOSTS file that acts as a database for resolving domain names. This malware has been fairly prevalent in Russia, but it has a global reach.
Other COVID-19 campaigns have used the same technique to invoke emotions in targets but, instead of claiming to have critical information from the CDC, they masquerade as webpages from financial institutions, travel sites, government tax agencies, and many others.
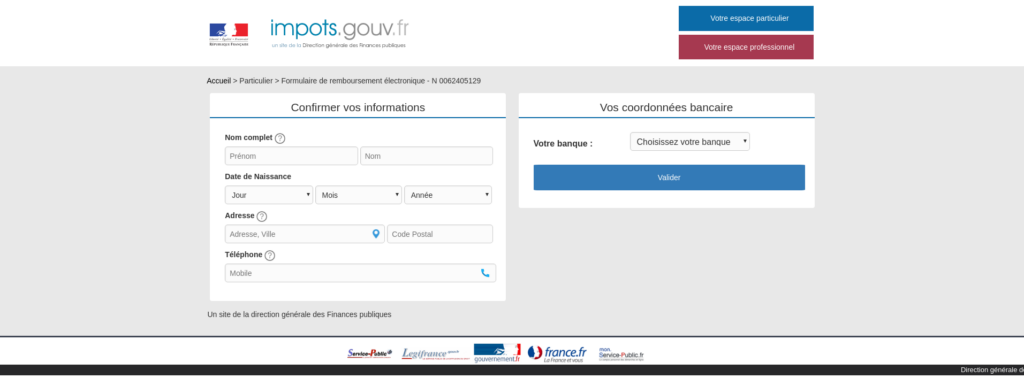
Here is a screenshot of a COVID-19 phishing webpage masquerading as the French tax authority. What a brilliant way to invoke multiple emotional triggers by combining COVID-19 with tax liabilities!
The good news is that now—with a little more awareness of how spear phishing and social engineering works—we will be a little better prepared to not fall victim to future phishing ploys.