The increased SEA attack surfaces for ransomware groups has prompted the cybercrooks into added blackmail or extortion into their arsenal.
To ensure that their victims will pay ransoms when hit by ransomware, cybercriminals have added blackmailing on their arsenal.
Top ransomware groups in the region have been targeting the following industries: state enterprises; aerospace and engineering; manufacturing and trading; beverage companies; palm products; hotel and accommodation services; and IT services.
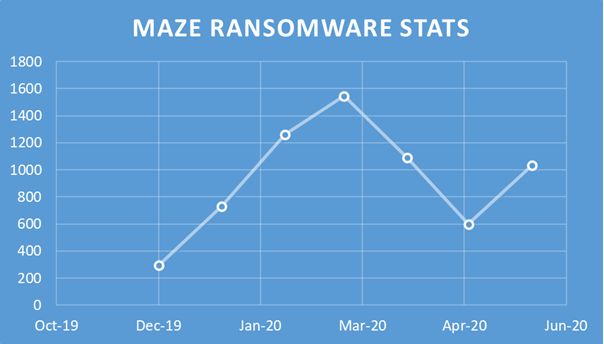
One of the first ransomware groups to add blackmail to their portfolio is the Maze family. The group behind Maze ransomware has leaked the data of their victims who refused to pay ransoms. The group leaked the data more than once in Nov 2019, with an additional warning that the published data was just 10% of what they were able to steal.
Aside from this, the maze ransomware group has also created a website where they revealed the identities of their victims as well as the details of the attack: date of infection, amount of data stolen, names of servers, and more.
Back in January, the maze ransomware group was involved in a lawsuit with a cable maker company. This resulted in the website being shut down.
Method of attack
The attack process being used by this group is simple. They will infiltrate the system, hunt for the most sensitive data, and then upload the treasure to cloud storage. Then the data will be encrypted. A ransom will be demanded based on the size of the company and the volume of the data stolen. The group will then publish the details on their blog and even make anonymous tips to journalists.
According to Vitaly Kamluk, Director, Global Research and Analysis Team (Asia Pacific), Kaspersky: “We are monitoring an uptick in Maze ransomware group detections globally, even against a few companies in Southeast Asia, which means this trend is currently gaining momentum. While the public shaming part of the attack adds to the pressure of bowing to the demands of these cybercriminals, I strongly advise companies and organizations not to pay ransoms and to involve law enforcement agencies and experts in such scenarios. Remember that it is also better to have your data backed up, your cybersecurity defenses in place, to avoid falling victims to these malicious actors.”
To remain protected against these threats, organizations can observe the following best practices suggested by Kamluk:
- Stay ahead of cyberthreats: make backups; simulate attacks for cyber-readiness; prepare an action plan for disaster recovery
- Deploy sensors everywhere: monitor software activity on endpoints; record traffic; check hardware integrity
- Never follow demands of the criminals. Do not fight alone: contact the relevant authorities
- Train various staff in remote-working cyber vigilance: digital forensics, basic malware analysis, PR crisis management
Finally, ensure that your cyber defense team follows the latest cyber threat trends via the multitude of reputable websites or threat intelligence subscription services.

















