Rise of independent attackers outside of the established RaaS groups presents a new set of challenges for organizations
Kroll recently published its Q1 2023 Threat Landscape Report, showing continued evolution in attack methods and fragmented threat actor groups.
The report found that the professional services sector reported a significant increase in cyberthreat incidents and observed a notable increase in the number of unique ransomware variants overall.
Sector analysis: Professional services swarmed
In Q1 2023, Kroll has observed a 57% quarter over quarter increase in the overall targeting of the professional services sector from the end of 2022.
Ransomware propelled this increase in the sector with legal firms reporting an increase in extortion and encryption attacks in Q1.
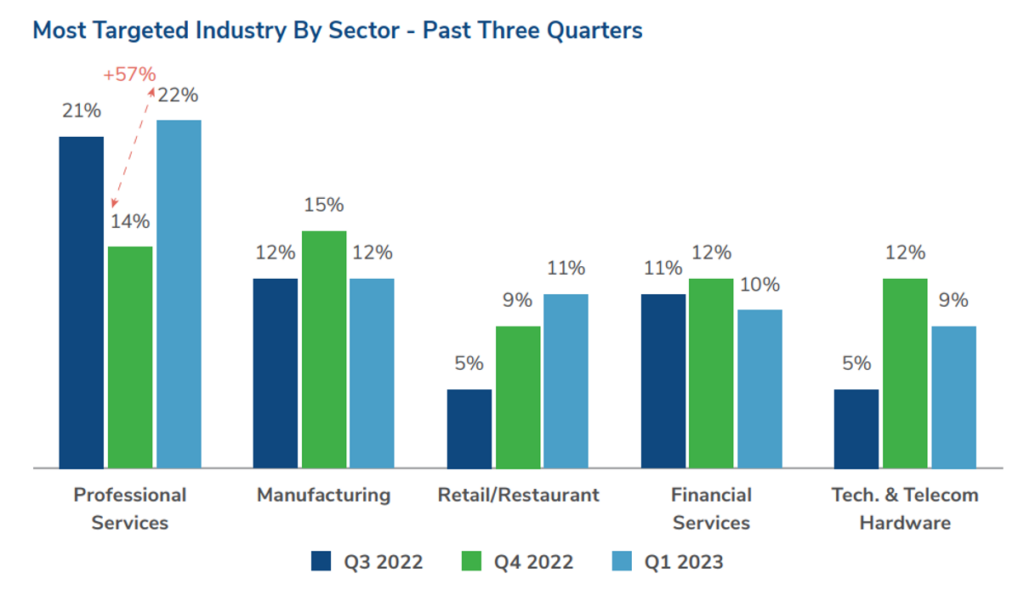
Professional services saw a 57% quarter over quarter increase and was the most frequent target of ransomware attacks in Q1 2023, while manufacturing continues to be another key target for ransomware gangs
Legal firms specifically felt much of the increased threat incidence this quarter. Similar to the Google Ads abuse tactic leveraged in many late 2022 attacks, Kroll observed an ongoing SEO poisoning campaign by the actors behind GOOTLOADER malware. GOOTLOADER infections typically led to large-scale exfiltration of sensitive data and, in some instances, extortion threats by established threat actor groups. The SEO poisoning campaign involved threat actors targeting legal professionals searching for standard contracts and templates.
Independent attackers taking a leaf out of the established RaaS playbooks
Ransomware continues to be the most impactful threat in Q1 2023, accounting for 30% of all cyber threat cases this quarter, followed by email compromises at 26%.
While well-known ransomware-as-a-service (RaaS) operations such as LOCKBIT continued to dominate the ransomware landscape, there was a 56% increase in “one-off” lesser-known independent threat actors targeting organizations with ransomware.
Some of these were new but others were established groups that had not been observed for several quarters.
“The rising number of ‘one-off’ ransomware variants means that time-constrained security teams will need to defend against a swarm of additional threat actors in addition to the major RaaS players. This increase is likely in part due to several RaaS groups being dismantled or fragmented, and the ease of entry for smaller threat actors to deploy ransomware,” said Paul Jackson, Regional Managing Director, Asia Pacific, Cyber Risk, Kroll.
“While the dismantling of major groups is positive news, our observations of lone actors or splinter groups in Q1 2023 clearly shows that the story is more nuanced, and that businesses should not be lulled into a false sense of safety from the news headlines. Lone-wolf actors can operate with less consistency and reliability than the more ‘established’ threat actor groups, hence making them harder to predict and making negotiations more difficult to anticipate. Promises such as provision of decryption key after payment of ransom are also not guaranteed.”
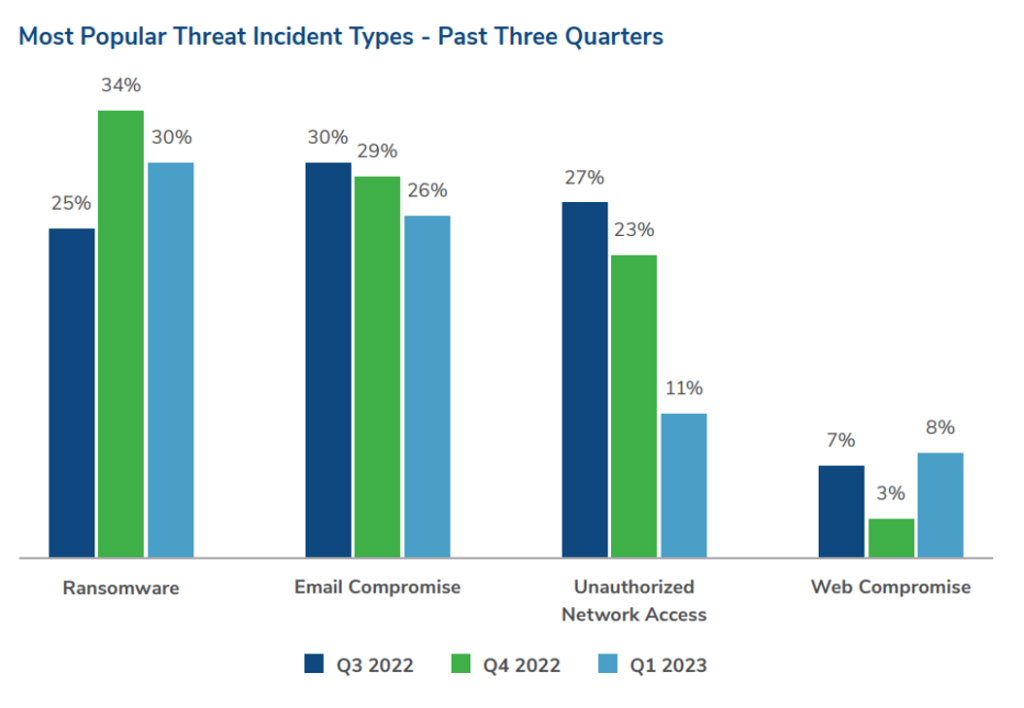
In Q1 2023, ransomware and email compromise continue to be the most impactful threats against organizations
Other key findings in the report include:
- This rise in unique variants included new variants such as CACTUS, DARKSKY and NOKOYAWA and other familiar – but not observed in the last several quarters – such as XORIST and RANSRECOVERY.
- Kroll detected an increase in the use of SLIVER in the quarter. Due to the public, open-source nature of this tooling, Kroll predicts SLIVER and other similar frameworks will continue to be deployed in more campaigns by threat actors.
- Kroll also noted a continued rise in web compromise, most typically against the retail sector, highlighting that threat actors for financial gain.
- Phishing continues to lead the pack when it comes to initial access across all cases.
“Phishing continues to be the main point of entry for hackers, so ensuring that employees are continuously trained in cybersecurity best practices and having powerful endpoint protection in place is a key first step in helping to prevent attacks.” Jackson added.
“No matter how actors get into a network, they are using exfiltration tools as standard across a wide variety of threat incident types. Detecting exfiltration of data and responding quickly can make the difference between a superficial data loss and a catastrophic one. It also serves as one of the last detection opportunities before ransomware deployment. Remaining vigilant using the right technology and in partnership with trusted security partners is a vital defense against the swarm.”

















