Better the threat group you know than the cyber-attacks you are not aware of…
A previously unknown cyber espionage group active in Asia, the Middle East and Africa since 2020 or earlier has been brought to light.
Named Worok by the researchers from ESET, the threat group targets firms from the telecommunications (East Asia), banking (Central Asia), maritime (South-east Asia), energy, military, government (the Middle East), private (southern Africa) and public sectors using the infamous ProxyShell vulnerabilities to gain initial access (in some cases).
After a significant break in observed operations from May 2021 to January 2022, Worok activity resumed in February 2022, targeting an energy firm in Central Asia and a public sector entity in South-east Asia.
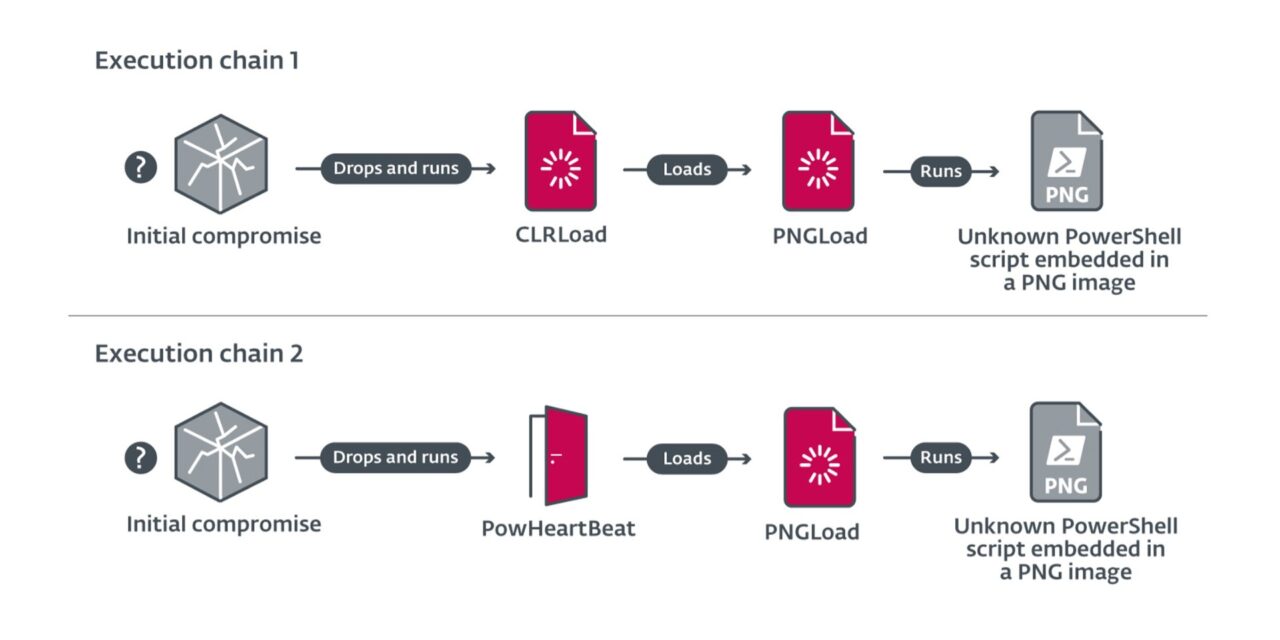
The threat group Worok is known to develop its own tools while also leveraging existing system tools to compromise its targets. Their custom toolset includes two loaders, CLRLoad and PNGLoad, and a backdoor, PowHeartBeat.
- CLRLoad is a first-stage loader that was used in 2021, but in 2022 it was replaced mostly by PowHeartBeat.
- PNGLoad is a second-stage loader that uses steganography to reconstruct malicious payloads hidden in PNG images.
- PowHeartBeat is a full-featured backdoor written in PowerShell, obfuscated using various techniques such as compression, encoding, and encryption. This backdoor has various capabilities, including command/process execution and file manipulation. For example, it is capable of uploading files to and downloading files from compromised machines; returning file information such as the path, length, creation time, access times and content to the command and control server; and deleting, renaming, and moving files.
Thibaut Passilly, the researcher who discovered the threat group, said: “We believe the malware operators are after information because they focus on high-profile entities in Asia and Africa, targeting various sectors, both private and public, but with a specific emphasis on government entities.”