Ransomware-as-a-Service is really inclusive: it lets all manner of malicious amateurs attack unsecure networks!
Some new Iranian threat actors have been spotted since June this year, using Dharma ransomware and a mix of publicly available tools to target companies in Russia, Japan, China and India.
All the affected organizations had hosts with Internet-facing RDP and weak credentials. The hackers typically demanded a ransom between 1 and 5 Bitcoins.
While Iran has always been known as a cradle of state-sponsored advanced persistent threat groups (APTs) for years now, the activities of the new group suggest that the country is venturing outside of politically-motivated agendas.
How they got noticed
During an incident response engagement for a company in Russia, threat-hunting firm Group-IB established that Persian-speaking newbie hackers were behind a new wave of Dharma distribution. Dharma, also known as Crysis, has been distributed under a Ransomware-as-a-Service (RaaS) model at far back as 2016. Its source code popped up for sale in March 2020, making it available to a wider malicious audience.
Even though the exact number of victims is unknown, the discovered forensic artifacts allowed Group-IB to establish the geography of the ransomware campaigns and the toolset, which is far behind the level of sophistication of big-league Iranian APTs.
Basically, the operators would scan ranges of IPs for hosts with Internet-facing RDP and weak credentials acrossRussia, Japan, China, and India. To do so, they used a popular software called Masscan, just as what Fxmsp, an infamous seller of access to corporate networks, used to do.
Once vulnerable hosts were identified, the attackers deployed a Russian tool NLBrute to brute-force their way into the system and to check the validity of obtained credentials on other accessible hosts in the network. In some attacks, they attempted to elevate privileges using the exploit in CVE-2017-0213.
What the hackers did
Interestingly, the threat actors likely did not have a clear plan on what to do with the compromised networks. Once they established the RDP connection, they decided on which tools to deploy to move laterally. For instance, to disable built-in antivirus software, the attackers used Defender Controland Your Uninstaller.The latter was downloaded from an Iranian software sharing website. Other tools were downloaded by the attackers from Persian-language Telegram channels when they were already present in the network.
To scan for accessible hosts in the compromised network, the group used Advanced Port Scanner—another publicly-available tool. After the network reconnaissance activities were completed, the hackers used collected information to move laterally through the network using the RDP protocol. The end goal of the attackers was to drop and execute a variant o these Dharma crysis ransomware: the adversary connected to the targeted hosts, then dropped the Dharma executable and executed it manually.
Said Oleg Skulkin, Senior DFIR Analyst, Group-IB: “The fact that Dharma source code has been made widely-available led to the increase in the number of operators deploying it. It is surprising that Dharma Crysis Ransomware landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage. Despite these cybercriminals using quite-common tactics, techniques and procedures they have been quite effective. Therefore, we believe it’s important to provide some recommendations on how to protect against them and give a complete outline of the MITRE ATT&CK mapping.”
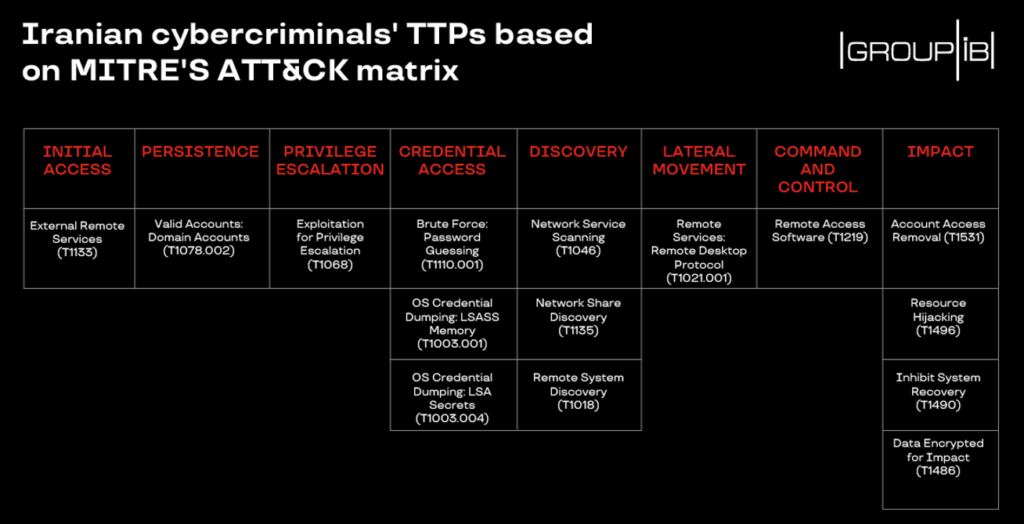
Protecting your network from Dharma Crysis Ransomware
If RDP has to be used, the default port 3389 should be changed. As the attackers usually need several attempts to brute-force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed log-in attempts per user.
Business should make sure their threat intelligence solutions are configured properly to mitigate risks and minimize damage by quickly identifying stolen data and tracking down the source of the breach. Specialized threat detection systems are available that can allow cyber defence teams to discover unwanted intrusions, traffic anomalies within the corporate network, as well as any attempts to gain unauthorized access to any data.

















