Emails from legitimate big-name services that pass domain-spoofing and typosquatting checks tend to put victims off their guard
According to one cybersecurity firm’s ecosystem data, the proportion of email-delivered-attacks (compared to web based attacks) had increased last year, reaching 86% of all file-based in-the-wild attacks.
While ransomware tends to attract more (negative) attention, the US Federal Bureau of Investigations had reported last year that Business Email Compromise (BEC) scams had cause damage totaling US$2.7bn in the country, compared to just US$34m for ransomware.
Meanwhile in Australia, the impact of BEC scams on victims has been significant, with financial losses totaling more than US$79m in 2021.
BEC tactics are evolving
These days, researchers from Avanan are observing a spike in what looks like a progression of such attacks: BEC Firm Impersonation.
In the past two months of February and March, the firm’s researchers saw a total of 33,817 email attacks impersonating legitimate, popular firms and services instead of actual high ranking corporate executives.
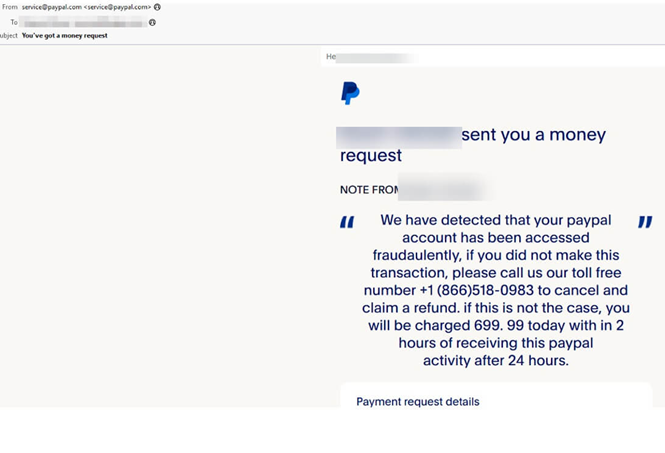
In this technique, hackers use actual legitimate services to carry out their attack. For example, all they have to do is create a free Google account, then can create a Google sheet and key-in the email address of an intended target. The latter will then receive an email notification from a totally legitimate service (e.g. PayPal, Google Docs) but within it is a link to a malicious site.
In all the attacks analyzed, the email address from which the BEC emails were sent looked perfectly legitimate and contained the “correct” domain addresses, which made detection and identification much harder for the average user receiving them. However, when the victim’s guard is down and activates a malicious link that looks like a standard Google Workspace or Microsoft 365 document link, the victim is directed to fake websites (phishing sites where credentials will be stolen), or a variety of other malicious attacks.