Could knowing how these advanced persistent threats operate lead to their eventual capture and downfall?
Forensic research on state sponsored cyber threat group SideWinder (also known as Rattlesnake, Hardcore Nationalist (HN2) and T-APT4) has uncovered its links to Baby Elephant, and the Donot advanced persistent threat (APT) groups.
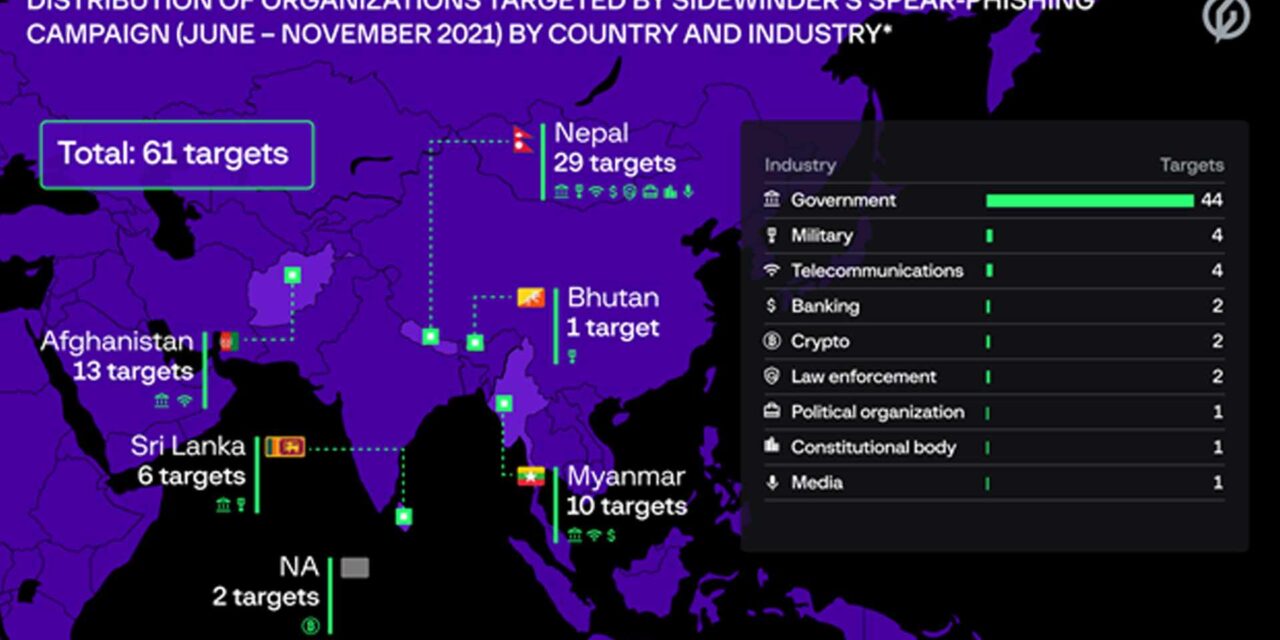
The research by Group-IB has also revealed Sidewinder’s role in targeting 61 government, military, law enforcement, and other organizations in Afghanistan, Bhutan, Myanmar, Nepal, and Sri Lanka, including a 2020 attack on the Maldivian government. The group also has interests in crypto crime.
According to one of the firm’s senior malware analysts, Dmitry Kupin: “We discovered that some indicators of compromise (for SideWinder) were related to another APT group, Donot, (but) were wrongly attributed to SideWinder. Nonetheless, we found additional evidence confirming that Patchwork (Hangover), Donot, and SideWinder sometimes borrow tools and malicious documents from each other and adjust them for their needs.”
Two phishing projects mimicking crypto companies were also found to involve SideWinder, possibly linked to the recent attempts to regulate the crypto market in India.
The group’s primary initial attack vector is spear phishing. Recent additions to its arsenal are SideWinder.RAT.b (a remote access trojan) and SideWinder.StealerPy, a custom information stealer. The perpetrators have been found to use the Telegram to receive data from compromised machines — an increasingly common trend among both APT groups and financially-motivated cybercriminals over the past year.
Believed to originate in India, SideWinder has been carrying out cyber espionage attacks against government organizations in the Asia Pacific region since at least 2012. More recently in June 2022, it launched a custom tool called SideWinder .AntiBot.Script that was used in phishing attacks against Pakistani organizations. Forensics also show that the group was behind several phishing projects designed to target government agencies in South-east Asia, among which were fake websites imitating the Central Bank of Myanmar between June and November 2021 or earlier. It is not known whether any of these phishing campaigns were successful.