They mimic legitimate apps so well you may not even have known the dangers! Is the store becoming a Pray Store?
A group of researchers have declared that some 10 million fraudulent apps (weeded out by now) have been downloaded from the Google Play Store for Android devices.
A large number of apps (164) were mimicking notable apps to garner downloads, only to then trick the user into seeing a whole bunch of unexpected ads.
These apps contain code capable of displaying out-of-context ads under the com.tdc.adservice package. The apps’ behavior is controlled by a command-and-control JSON hosted on Dropbox (Note: Dropbox is another victim, not a participant, in the research operation).
The URL of the JSON differs from app to app, but the structure is very similar, indicating the frequency of the ads and the Publisher ID to be used.
Flying under the radar
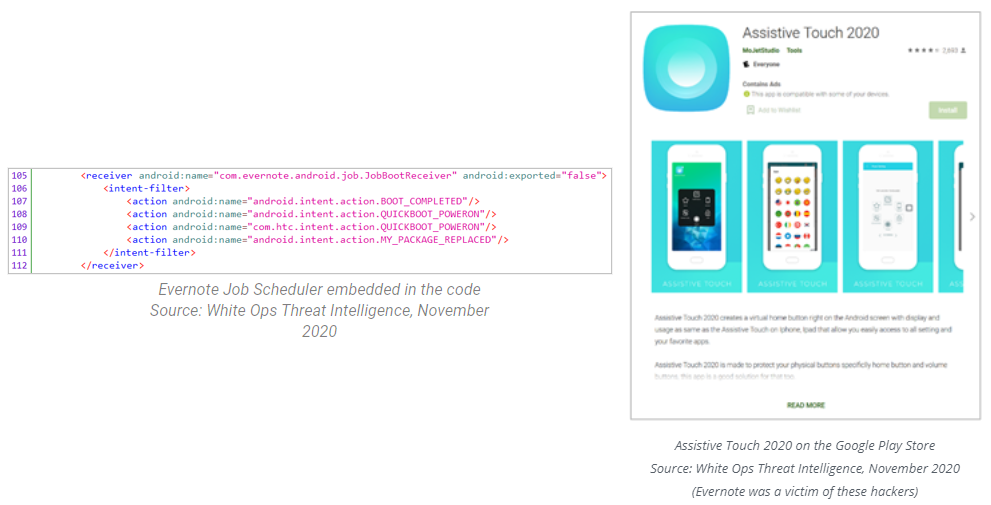
Named after a legitimate app called Assistive Touch, an app called Assistive Touch 2020 contained an open-source Evernote job scheduler embedded inside for use as a persistence mechanism.
A quick lookup for Evernote jobs led the researchers from the Satori Threat Intelligence and Research Team to the entry point of the out-of-context ads controller located inside the AdsJob class. Based on the configuration received from the server, the job displays either in-house ads or out-of-context interstitials.
According to the team consisting of Gabi Cirlig, Michael Gethers, Lisa Gansky and Adam Sell, the ads being displayed are retrieved dynamically from a JSON hosted in the cloud when the app is first launched, and then again at regular intervals. It is then stored inside the shared preferences of the app with the data being proxied through the AppConfig class.
By leveraging legitimate tools used by developers to establish persistence and instantiation of the out-of-context ads, the authors of the SDK managed to fly under the radar for at least two years.
Modus operandi
Once the app is installed, it reaches out to the command-and-control server, which controls how often the ads are displayed, whether ads to in-house products are displayed; and the platform from which the interstitial should be retrieved.
After a grace period of several hours (depending on the command-and-control server’s configuration), out-of-context interstitials start appearing on the device.
The out-of-context interstitial excludes itself from the list of recent apps, and as soon as the user navigates away from it, it disappears.
Watch what you download
The Satori Team recommends blocking any apps that call ads from activities inside the package com.tdc.adservice.*. Even though platforms could choose to allow legitimate traffic from these apps by blocking only the out-of-context ads, the Satori Team recommends using the heavier-handed approach of blocking all the apps, since they were likely created very specifically to take advantage of the digital ecosystem.
When downloading any app, make sure that you are getting the real, official version. Look at the reviews: not just the glowing five-star reviews, but also the one- and two-star reviews. Those are the ones that will call out ads that do not belong, and will alert you if something is amiss.
Fraudulent apps and their package names


















