The school in the APAC region had felt fully protected but wanted to understand how AI may tighten protection further.
An academic institution had installed spam protection, URL protection and the full Mimecast package across the email realm. Interested to explore how AI solutions may bolster their network security further, it had sought advice from a vendor.
Ironically, just two days before that vendor meeting, the school was hit by a business email compromise (BEC) attack. An attacker had taken over a staff’s Microsoft 365 account and sent a fraudulent invoice to the organization’s accounts department. The invoice, which contained subtly-edited bank details, claimed to be from Siemens, one of the world’s leading automation technology companies. Given that Siemens was an established supplier of the school, the attack succeeded.
The academic institution’s staff unwittingly paid over US$60,000 into the attacker’s bank account.
A nearly identical BEC attack arrived a week later, but this time, the school’s inbox had been armed with a new AI solution from Darktrace that succeeded in neutralizing any harm.
Analyzing the second attack
On this occasion, unusual behavior on a compromised SaaS account together with suspicious email activity caused several Darktrace models to fire, culminating in a 73% anomaly score and the decision to autonomously hold back the offending email.
The initial compromise occurred on Tue April 21 04:15:40 when the AI solution first detected something was amiss when a SaaS login was seen from an unusual IP address located in the UAE.
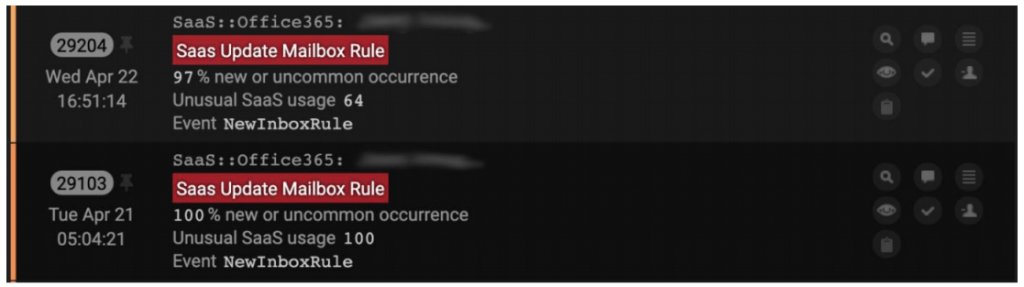
It then noticed a behavior commonly associated with BEC — the creation of an inbox processing rule so that if anything came from the actual vendor, it would be deleted and redirected to the threat-actor.
This initial compromise led to a very targeted spear phishing campaign. The attacker found an authentic email chain regarding an invoice from the domain siemens.com. Using the trusted supplier’s reputation, they copied the exact format of the invoice and then created a spoofed domain ‘siemesm.com’, intending to target the accounts team at the organization with a fresh invoice—but with one important detail changed – the bank details.
The attacker was careful. Before launching the attack, they sent a test email on April 22 to the compromised account to ensure it was getting through. This email was tagged with a 38% anomaly score.
The following morning, the attacker set up some fake correspondence between the newly-created account and the targeted staff, before looping in the accounts team with a new request—this time, asking for US$78,000. Again, the exchange appeared legitimate: from a well-known supplier, and with the apparent ratification of a trusted colleague.
Here, we can see the AI email security solution growing gradually more suspicious of this unusual behavior over time. The high anomaly scores assigned to the suspicious email was influenced not only by the lack of previous correspondence between the two email users, but also the email rules that were made on the account itself the previous day.
Furthermore, the AI solution recognized the email as a fake reply: not a direct response to the email, but one which attempted to replicate it by copying and pasting correspondence from a separate email chain. The last phase of the second BEC attack was launched and foiled on the same day—23 Apr 2020.
When an attack fails, go island hopping
The attackers soon realized their attack had failed, and then leveraged a technique known as ‘island hopping’. This involved harvesting the company-wide contact list and proceeding to launch a more generic phishing campaign to dozens of email users across the company — hoping in turn to compromise their accounts. Again, the newly installed AI email security solution (Antigena Email) deemed every one of the island hopping emails as 100% anomalous and held every single email back.
While this was a relatively advanced attack with multiple stages, the techniques described herein represent nothing exceptional in an AI-secured email infrastructure in use by hundreds of organizations around the globe.
By deploying such solutions into their email environments, IT teams and cyber defenders can have strong visibility over internal and external mail flows, plus the ability to stop targeted and sophisticated attacks before escalations into a crisis.

















