What you should do when unsolicited bug bounty hunters demand payment for identifying your system vulnerabilities…
You are probably familiar with the popular practice of “bug bounty” programs in software security. Typically, the more severe the flaw, the higher the bounty.

A rising trend now is called the “beg bounty”, and they are definitely not benevolent! What are they and why are they such a menace? These are queries that range from honest, ethical disclosures to borderline extortion demands.
According to a principal research scientist at Sophos, Chester Wisniewski, the trend started in the middle of 2020, when more and more security researchers were making unsolicited contact with businesses about vulnerabilities in their website.
“Knowing these businesses did not have a bug bounty program and in fact probably didn’t even know what code ran their website, it seemed odd for a legitimate researcher to be wasting their time on the smallest fish in the pond,” Wisniewski recalled. As a threat researcher, he nevertheless did some poking around to find out more.
The Beg Bounty playbook
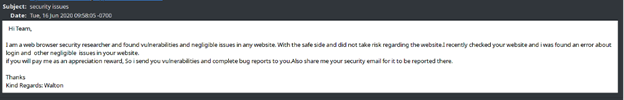
In the example below, the unsolicited ‘vulnerability report’ or beg bounty was sent to an email address available openly on the recipient’s website. It was not hard to conclude that each message was a combination of:
- Automated scanning for basic vulnerabilities or misconfigurations
- Followed up by a human to cut and paste the results of the scan into an email template
- Figuring out where to send the report to try and receive a reward
In another example, the writer claims to have found a ‘vulnerability in your website’ and then goes on to explain that the organization does not have a DMARC record for protection against email spoofing. That is neither a vulnerability nor is it in the website. While publication of DMARC records can help prevent phishing attacks, it is not an easy policy to deploy, nor is it high on the list of security tasks for most organizations. The author, however, is undoubtedly more detailed than the first example cited, and at least tries to be helpful, hoping the organization may be interested in a further security test or relationship.
One more example of beg bounty approaches involved the author provides a proof of concept (PoC), explains the impact and how to fix the issue. The explanatory text is clearly cut and pasted from websites that teach how to perform this type of basic tests/attacks. This kind appeared to be the most legitimate of the examples, and upon engaging with the author, Wisniewski found that the bounty beggar was sincere and seemed genuine in quoting US$150 to $2,000 per bug fixed. However, a known consequence of paying such ‘sincere’ beg bounties is that they can escalate and become more threatening in future.
One organization apparently said it started out at US$500 and then, as further bugs were reported, the senders quickly demanded $5,000 and were more threatening.
Scaremongering for profit
According to Wisniewski, none of the vulnerabilities he investigated were worthy of a payment. “The problem is that there are millions of poorly secured sites owned by small businesses that do not know any better and are intimidated into paying for services out of fear,” he noted.
His advice for organizations that receive beg bounty emails: If your organization receives one of these emails, it is likely have the company may have a very poor security posture and should take this shortcoming seriously. However, you should not engage with the person soliciting your business but instead you should contact a local trustworthy firm to assess your security weaknesses and work with you to prioritize and improve the situation.