Spoiler alert: tips include reducing dwell time, clearing up clouded responsibilities, adopting zero-trust, pen testing, and assuming insider threats.
In 2018, cybercrime accounted for 18% of all crime in Singapore, increasing steadily over the previous two years, according to the Cyber Security Agency of Singapore (CSA).
As companies in Singapore and across the region fight to combat this trend, are looking to bolster their defences, IDC reports that spending on security related hardware, software, and services in the Asia Pacific region—excluding Japan—will increase at a five-year compound annual growth rate of 20.1% between 2017 and 2022 to reach US$ 28.2 bn by 2022. To help enterprises to be adequately protected across hybrid, cloud and on-premises environments, here are my five tips that will help security professionals create a smarter enterprise security posture.
- Prevention is a pipe dream
With data breaches on the rise, organizations are increasingly shifting their strategy from protection and prevention at the perimeter to detection and response in the east-west traffic corridor. This makes effective incident response a top concern for security and risk professionals, according to Gartner. The company estimated that 60% of all enterprise information security budgets would be allocated to rapid detection and response approaches by 2020, compared to less than 10%in 2014. While prevention still has value as a prudent first line of defense, cybersecurity leaders should re-focus their operations—people, process, and technology—on reducing dwell time after a breach and mitigating damage.
- Get clarity on cloud security
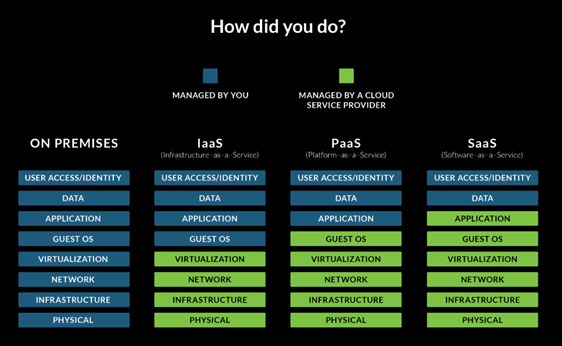
If your organization is hosting anything in the cloud, it is critical to understand where your cloud service provider’s security responsibility ends and yours begins. In reality, cloud security is a shared responsibility with the cloud service provider to protect on-premises, infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS). Some of the most common threats to cloud security are homegrown and preventable, including misconfiguration, unauthorized access, and insecure APIs.
- Trust no one, not even your vendors
Enterprises rely on third-party tools for everything from infrastructure and applications to security, but do these organizations know how vendors use their data? Security and IT organizations seldom realize how often and in how many ways their data is sent by vendors to vendor environments, which can have legal and regulatory ramifications.
When looking at all the activity on an enterprise network, we see a frequent pattern of vendors ‘phoning’ or ‘calling’ data home. This is a white hat term for exfiltrating data to their environments—a practice that is not problematic at face value. Vendors phone customer data home for a variety of legitimate and useful reasons with the customer’s advance knowledge and approval, and do so securely through de-identification and encryption.
However, phoning data home becomes problematic when enterprise customers are unaware that certain sensitive data, like personally identifiable information (PII) are leaving their environment, or that the vendor is phoning home data at all. This is a lot more common than one would like to believe. Companies must question vendors to understand how data is being handled, where it is going, and what level of encryption the vendor uses.
- Test your defences
To improve the security posture of your organization and find potential gaps in your defences, run red versus blue exercises. Red teams are external entities brought in to test the effectiveness of a security program. They are hired to emulate the behavioral traits and techniques of likely attackers to make it as realistic as possible, while the blue team belongs to the internal security team that is charged with stopping these simulated attacks.
These keep security teams sharp and help proactively identify your security vulnerabilities.
- Assume the threats are already inside
In 2018, the Asia Pacific region was exposed for being slower to detect breaches than other regions, with a median dwell time for organizations being five times longer than the global average. Businesses must invest in capabilities that allow them to monitor and analyze traffic inside their networks actively. This is where threats dwell, and right now it is an open field for attackers.
As businesses continue digital transformation initiatives, security and risk professionals will need to adopt new ways of thinking to protect organizations. Companies must also remain vigilant about new and emerging threats that could have significant impact on the business if not identified and addressed quickly.