Existing perimeter and endpoint security solutions need a powerful overarching framework based on changing outdated mindsets, says this expert.
The growing threat of cyberattacks is hindering the pace of digital transformation, with as many as three in five businesses in Asia Pacific region putting off digitalization plans out of fear of being targeted by cybercriminals.
According to a Deloitte businesses report, this could result in a potential loss of US$145bn in GDP growth in Asia Pacific over the next decade.
Although enterprises have increased investments in security solutions, bad actors nevertheless have the resources and the time to poke holes in any enterprise security strategy at any given moment. Furthermore, most approaches to cybersecurity today are still too reactive and too focused on chasing threats. For these reasons, it is critical for organizations to rethink security architecture across core infrastructure, applications, users and operations.
For starters, organizations need to debunk common security misconceptions that prevent enterprise-wide integration of cybersecurity into core business strategies. Following are seven misconceptions that every CIO needs to take note of.
- Misconception #1
“A deep understanding of attack trends helps us protect more effectively”
Traditional approaches to security are largely reactive. They heavily emphasize processes and techniques to better understand attackers, prevent common-type attacks, and mitigate damage after the fact. However, this reactive mode is outdated—if it ever worked at all.
Instead of trying to understand an attacker’s intent, organizations should proactively examine their own environment and identify the apps and data that need the most protection. Understand those workloads and focus on an application’s intent. Then, give those workloads specific parameters that are built on the concept of monitoring and enforcing “good” application behavior rather than on the aim to identify and mitigate “bad” behavior. - Misconception #2
“Security is primarily the responsibility of the security team”
As data, systems, and applications touch every corner of the business, security should be an enterprise effort led by a spectrum of teams and functions across infrastructure, architecture, network, application, security, and lines of business.
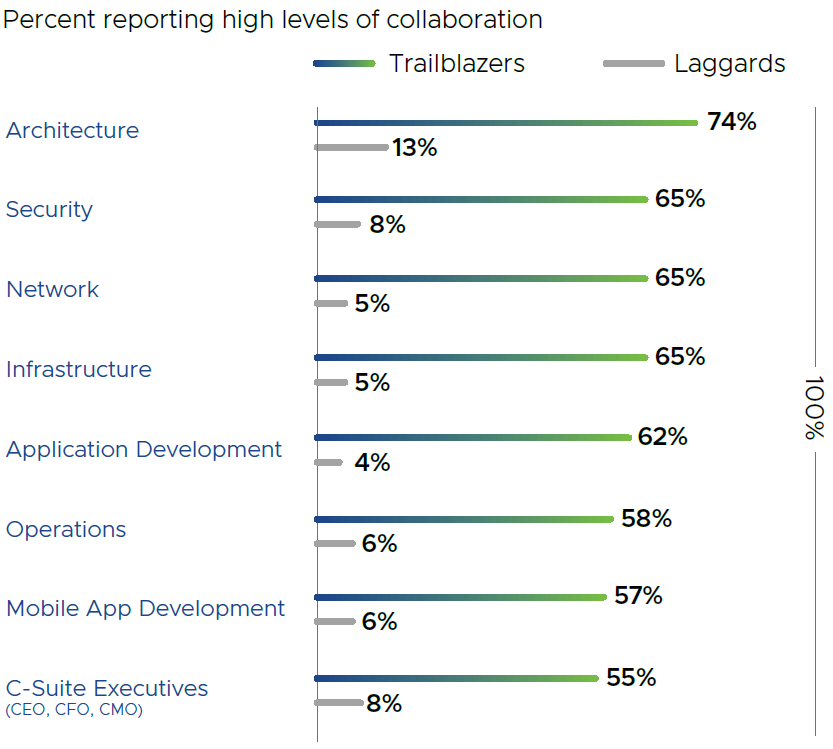
Already, leading organizations are leveraging DevSecOps models to foster collaboration across development, operations, and security teams in application rollouts. A recent Forbes Insights security survey underscored the importance of collaboration across all IT functions. Unsurprisingly, cybersecurity trailblazers blew laggards out of the water when it came to levels of collaboration within the organization (Figure 1).
Once cybersecurity becomes a collaborative organizational priority, the dedicated security team can concentrate on tasks of higher value, such as testing new security innovations or working with the legal team to interpret and adhere to ever-changing regulatory and privacy laws.
- Misconception #3
“Security teams are best placed to decide which digital assets to protect”
Security teams, despite their technical expertise, need help understanding which digital assets are most critical across various parts of the business. Otherwise, they will attempt to protect everything equally—a costly and eventually fruitless exercise.
By implementing a Zero Trust policy, the team operates on the principle of trusting nothing and verifying everything that is trying to access systems inside or outside its perimeters. In an environment of distributed apps, users, devices, and networks, an enterprise-wide focus on a Zero Trust policy for application behavior, devices, and access will be critical. - Misconception #4
“Boards will not approve the necessary budget for security”
Boards will respond positively to requests for security funds—but CIOs must frame such requests as risk-management exercises that directly impact the business, rather than as additional technology investments. Boards are used to managing a myriad of risks—geopolitical, financial, and market risk. Adding cybersecurity to that list is a logical step.
While there is no silver bullet for cybersecurity, it is critical to explain to the board why there is a need for organizations to continue investing in this area. A recent VMware report unveiled that there is opportunity to grow APAC’s GDP by US$145 billion over the next 10 years if enterprises adopt an intrinsic security approach that ensures business continuity and greater adoption of new technologies. - Misconception #5
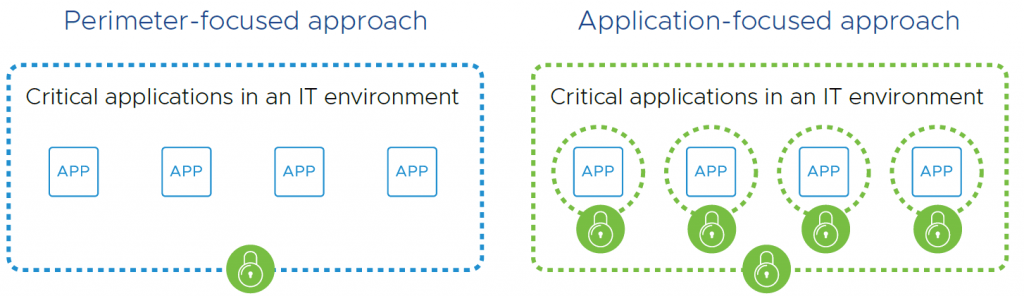
“Organizations can best secure themselves by protecting infrastructure and the perimeter”
Current approaches to protecting data and apps focus on protecting the actual IT infrastructure. However, with the advent of technologies—including cloud, distributed modern applications, and microservices architectures—app components can be scattered across multiple machines. By focusing on protecting infrastructure rather than the apps or data themselves, CIOs are operating with a disconnected—and flawed—security model. As such, it is imperative for CIOs to move to an application-focused security model.
- Misconception #6
“Users are the biggest security problem”
While sufficient and frequent training are still important and necessary, attackers today have become much more sophisticated. The reality is that users can get infected from just hovering over (not clicking) links. Attackers can get into mail servers and send malicious attachments using the credentials of someone a user knows and trusts.
Despite the evolving threat landscape, many organizations still over-provision access rights to apps and data and yet do not have safeguards that monitor admin access. In this situation, having strong authentication and identity management safeguards in place should be a mandate. Identity should be verified using multiple factors, and authentication should be commensurate with the risk of the requested access or function for an individual application. - Misconception #7
“Security by necessity impedes business agility”
While most businesses have moved on to Agile software development methodologies, the speed of security review for apps has not increased.
A huge opportunity to jumpstart innovation exists here. With today’s automation tools, DevOps teams can push out app updates to the security team in real time. Security teams then perform their review, and push the app out to production. Organizations are becoming more agile with robust, intrinsic security because security gets simpler, faster and more effective when framed around applications and data—as opposed to infrastructure. However, this requires organizations to shift their thinking.
Although debunking these misconceptions is a good first step for organizations, it is just a first step. Security is a never-ending journey and it requires long-term commitment.
Enforcing security via application behavior is a radical, new approach to security, but it is also complementary to the frameworks that exist today. Intrinsic security does not mean abandoning your investment in existing perimeter and endpoint security solutions. Instead, it is an additive step that makes an organization’s security posture considerably more robust.