And hackers now have a new theme to scam with: COVID-19 vaccinations—according to one cybersecurity firm.
The fresh and expanded attack surface opened by remote-working arrangements around the world finally culminated in a 768% cumulative increase in Remote Desktop Protocol (RDP) attacks in between Q1 and Q4 2020, with the rate slowing in the last quarter, according to the client data of cybersecurity firm ESET.
Another trend observed in Q4 was an increase in COVID-19-themed email threats, especially related to the end-of-year vaccine rollouts. The latter offered cybercriminals an opportunity to extend their portfolios of lures used, a trend that is expected to continue this year.
Explained Roman Kováč, the firm’s Chief Research Officer: “RDP security is not to be underestimated especially due to ransomware, which is commonly deployed through RDP exploits, and, with its increasingly aggressive tactics, poses a great risk to both private and public sectors. As the security of remote work gradually improves, the boom in attacks exploiting RDP is expected to slow down—we already saw some signs of this in Q4.”
Also, according to the firm’s research for Q4, a previously unknown advanced persistent threat group XDSpy had started targeting the Balkans and Eastern Europe; supply chain attacks were also on the rise, in the form of a Lazarus attack in South Korea, a Mongolian supply-chain attack named Operation StealthyTrident, and the Operation SignSight supply‑chain attack against a certification authority in Vietnam.
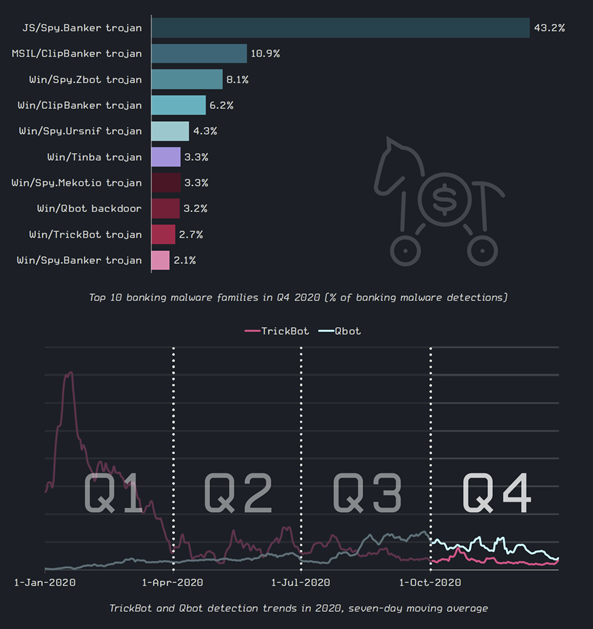
Finally, in Oct 2020, the firm had been part of a global disruption campaign targeting TrickBot, one of the largest and longest-lived botnets. The coordinated efforts resulted in 94% of TrickBot’s servers being shut down in a single week. “There was a sharp decline in TrickBot’s activities following the disruption operation late last year. We are continuously monitoring the TrickBot botnet, and the level of activity remains very low to this day,” commented the firm’s Head of Threat Research, Jean-Ian Boutin.





















