At least this is what the 10-year telemetry in a cybersecurity firm user base shows.
14 October 2021
Analysis of historical data within a cybersecurity firm’s user ecosystem has linked the increased use of cashless payments in the Asia Pacific region (APAC) with the rise of banking trojan in the region.
In the malware world, banking trojan are some of the most dangerous species as they are used to perpetrate theft from users’ bank accounts, according to Vitaly Kamluk, Director of Global Research & Analysis Team (GReAT) for APAC at Kaspersky.
The goal of this type of malware is either to obtain access credentials or one-time passwords to online bank accounts, or to manipulate the user and hijack control for the live online banking session from the legitimate owner. “As we all know, the (pandemic) lockdown restrictions forced everyone to shift their financial transactions online. But, now, after analyzing the historical figures we have on financial threats, I also learned that there was another outbreak that started in early 2019 in APAC: banking trojans,” Kamluk said.
Telemetry from Kaspersky’s security network shows that this malicious threat has grown in terms of detections and reach: Kamluk predicts that it will continue to pose a significant threat to both financial organizations and individuals in APAC as more users and startups start dipping their feet into the digital payments field.
Telemetry specifics
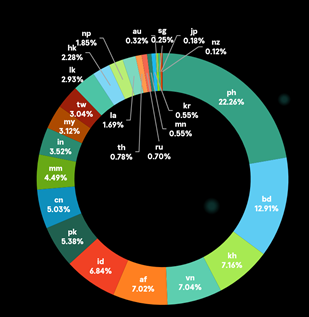
Here are data specific to the region:
- South Korea was among the pioneer countries in APAC that suffered from banking Trojans throughout 2011–2012. However, since 2013 the country had showed significantly low relative numbers of infections and the Kaspersky ecosystem there currently had the lowest levels of banking trojan of countries in the region.
- The firm’s cybersecurity user networks in developed countries showed low statistics of banking trojans detection, while developing countries seemed to have become and remain a hotspot for cybercriminals since 2019.
- In terms of regional distribution, the Philippines logged the highest number of unique users attacked in APAC at 22.26% of all banking trojan discovered in the region, followed by Bangladesh (12.91%), Cambodia (7.16%), Vietnam (7.04%), and Afghanistan (7.02%).\
- Based on analysis of almost 300 publicly reported financial sector cyber incidents since 2007, the cybercriminals were of several genres:
- Non-state actors: individuals or criminal groups seeking personal gains and illegal profit. Often interested in unauthorized access to sensitive payment processing systems, ATM networks, but also running blackmailing after DDoS or ransomware attack. The result of such attacks are either disruption of business operations or money theft.
- State-sponsored: organized skilled hackers, more likely on a payroll. Their job is to sneak behind enemy lines at other nations’ sensitive networks to map assets, install malicious backdoors, and even to conduct massive financial heists in some cases.
- Insiders: these threat actors spend their work days stealing corporate intellectual property, either to resell for personal profit or to further the objectives of the nation-state that employs them.
- Multiple actors: a combination of the abovementioned types.
- Unknown: this is not an attacker type by itself—it simply includes all cases where it was not clear who was behind the attack.
According to Kamluk, the proportion of the unknown groups has grown over time, which is an alarming trend. With the growth in the number of cyber attacks, there seems to be an alarming trend of financial institutions becoming less and less capable of identifying who attacked them: “The unknown, unidentified threat actors were behind 60% of the attacks in 2020, but this number will likely grow up to 75% this year.”





















