If NotPetya was terrifying, SUNBURST must have been a nightmarish wake-up call to mandate DNS logging and stop trusting “trusted” platforms.
During the months before the SolarWinds SUNBURST exploit was discovered late last year, significant increases in suspicious network activity went largely ignored due to the privileged and trusted status of SolarWinds within the IT industry.
This post-disclosure finding by ExtraHop points to another lapse in cybersecurity linked to human judgement: disabling DNS logging.
As part of the findings report, ExtraHop also released an expanded list of over 1,700 SUNBURST indicators of compromise (IOCs) as observed across affected environments protected by their systems, which may be useful in helping organizations determine if and to what extent they have been compromised.
A study in evasion techniques
During its investigations, and through its work with customers to help detect and remediate the SUNBURST exploit, ExtraHop threat researchers found that between late March 2020 and early October 2020, detections of probable malicious activity had increased by approximately 150%.
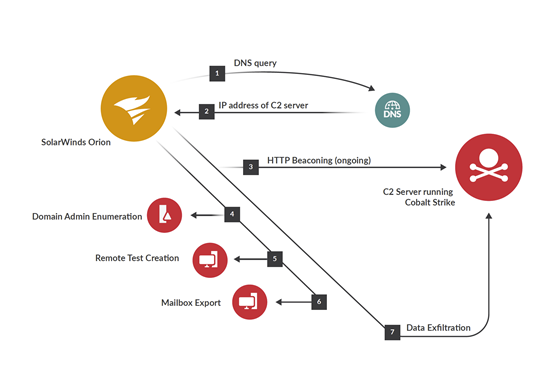
These detections included lateral movements, privilege escalations, and command and control beaconing, but they evaded the more traditional detection methods like endpoint detection and response (EDR) and antivirus solutions. Activity patterns indicated that the attackers were successful in flying under the radar of these detection methods either by disabling them, or by redirecting their approach before they could be detected.
Said the firm’s Deputy CISO, Jeff Costlow: “What we found when investigating SUNBURST was that the activity was actually detected on the network, but because other detection methods were not alerting on the activity, it largely went ignored. In this case, the attack was strategically designed to evade those detections, and we can expect more similar attacks to follow. It’s an important reminder that the network doesn’t lie.”
In addition to shedding new light on how the attackers were able to dwell within the network unchecked for so long, the report delves into how organizations used historical metrics to determine the duration of the compromise, as well as which systems and data may have been impacted.
Disabling DNS logging was a lapse
Despite extensive investigations, a corporate victim of the attack had turned up nothing. Shifting their view to the network, they got two hits. They had already been searching their environment for any sign of SUNBURST activity, so why had they not uncovered it sooner?
Their primary source of data was activity logs, which one might expect to have turned up any IOCs. However, the latent SUNBURST code was communicating with its C2 server through DNS. This technique made it difficult to detect, since DNS is a noisy protocol. Its frequent traffic also means that keeping records of DNS in logs requires a lot of storage capacity, and making that data easy to sort through for investigative purposes is a nontrivial challenge as well.
Not surprisingly, this victim organization, like many, had not enabled logging on DNS, thereby leaving a blind spot that SUNBURST took advantage of.
A massive lesson to be learned
If NotPetya was a terrifying anomaly, SUNBURST must have been a nightmarish wake-up call. According to the report, even strong security best practices like zero trust and network segmentation are not enough when people start assigning elevated privileges and turning off monitoring for IT solutions like Solarwinds that are “trusted”.
Traditional sources of security data such as logs and events leave major blind spots within modern networks. Some legacy protocols do not log at all and many devices cannot be instrumented.
Advanced threats, including supply chain compromises, require heightened awareness, continuous, real-time visibility, and the ability to quickly respond to threats inside the network. Leveraging network metadata is the only way an organization can deal with the constant opacity of legacy protocols and mismatched security tools.