What do the inkblots tell you? Rorschach ransomware lets everyone see something different…
Check Point Research (CPR) have detected a previously unnamed ransomware strain, which its researchers nicknamed “Rorschach”.
CPR and Check Point Incident Response Team (CPIRT) are drawing attention to the ransomware, which was recently deployed in an attack against a US-based company.
Rorschach encrypts nearly twice as fast as LockBit. More sophisticated than traditional ransomware, Rorschach combines tactics from multiple well-known attacks plus new unique features for maximum damage and evasion from cybersecurity solutions.
The ransomware was deployed using DLL side-loading of Palo Alto Network’s Cortex XDR, a signed commercial security product, in a loading method not commonly used to load ransomware. CPR has since notified Palo Alto Networks of the vulnerability in the product.
Inkblot test: everyone sees something different
Unlike other ransomware cases, the threat actor did not hide behind an alias and appears to have no affiliation to any of the known ransomware groups. Those two facts, rarities in the ransomware ecosystem, piqued CPR’s interest and prompted its researchers to thoroughly analyze the newly discovered malware.
What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware.
Sergey Shykevich, Threat Intelligence Group Manager, CPR, commented: “Just [like] a psychological test, Rorschach looks different to each person. This new type of ransomware has high levels [of] technically distinct features taken from different ransomware families – making it special and different from other ransomware families.”
He added: “This is the fastest and one of the most sophisticated ransomware we’ve seen so far. It speaks to the rapidly changing nature of cyber-attacks and to the need for companies to deploy a prevention-first solution that can stop Rorschach from encrypting their data.”
Previously unseen speed, rarely seen features
Interestingly, Rorschach was deployed using DLL side-loading of Palo Alto Networks’ Cortex XDR Dump Service Tool, a signed commercial security product. This loading method is not commonly used to load ransomware, and reveals a new approach taken by cybercriminals to evade detection.
Analysis of the new ransomware revealed its unique features. A behavioral analysis of the new ransomware suggests it is partly autonomous, spreading itself automatically when executed on a Domain Controller (DC) while it clears the event logs of the affected machines.
In addition, it’s extremely flexible, operating not only based on a built-in configuration but also on numerous optional arguments which allow it to change its behavior according to the operator’s needs.
While it seems to have taken inspiration from some of the most infamous ransomware families, it also contains unique functionalities, rarely seen among ransomware, such as the use of direct syscalls.
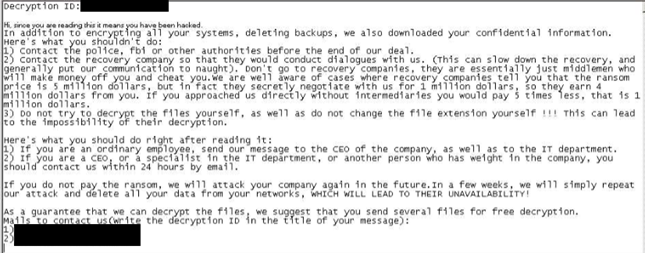
The ransomware note sent out to the victim was formatted similarly to Yanluowang ransomware notes, although other variants dropped a note that more closely resembled DarkSide ransomware notes (causing some to mistakenly refer to it as DarkSide).
Each person who examined the ransomware saw something a little bit different, prompting CPR to name it after the famous Rorschach psychological test.