Even though vulnerabilities were stopped in time, developers need to remain vigilant against supply chain risks in accessing open source repositories
Recently, a vulnerability has been discovered in the widely used software repository GitHub, that, when exploited could allow attackers to take control of a repository and insert malicious code in all applications and other programs that depend on it.
According to the Checkmarx Supply Chain Security (SCS) team that disclosed the vulnerability, GitHub’s “Popular repository namespace retirement” mechanism contained a vulnerability that could have led to attackers taking control over thousands of open-source packages. Also:
- The Go, PHP, and Swift languages alone have more than 10,000 packages that are vulnerable to this attack vector. The practical meaning of that is that thousands of packages could have been immediately hijacked and used to start serving malicious code to millions of users and many applications.
- This was not the first vulnerability found in the repo-naming mechanism; earlier this year, an attacker had used a similar vulnerability to hijack and poison popular PHP packages found in millions of downloads. The vulnerability was subsequently classified as “high severity” and a fix was released thereafter.
- The “Popular repository namespace retirement” exploit remains an attractive attack point for supply chain attackers, and open source tools are available for developers to use for identifying and reporting on any future vulnerabilities.
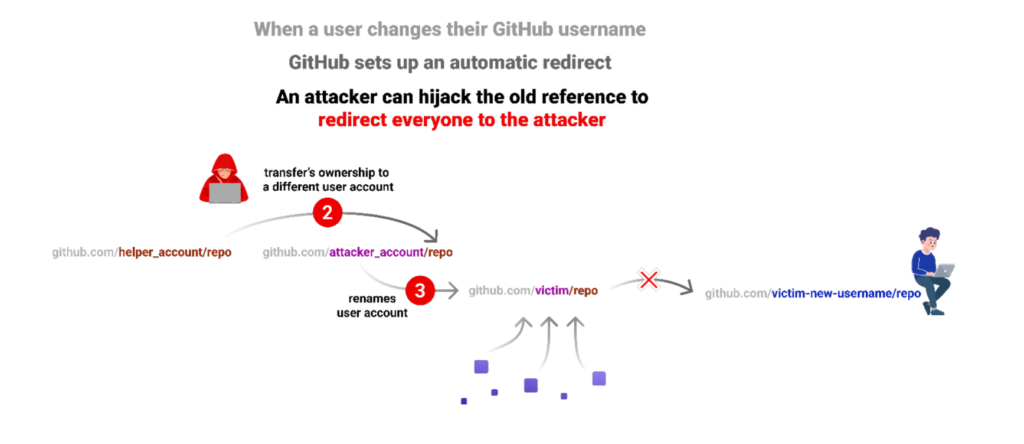
While this vulnerability has been patched and is no longer exploitable, the inadvertent use of retired namespaces is still considered a risky practice due to lingering vulnerabilities that have yet to be discovered.
The firm’s CISO, Peter Chestna, advises: “Having the right tooling to provide the needed telemetry, combined with strong engineering practices and security controls, is essential to understanding and managing (software supply chain risks). Leverage application security solutions running in the background to safeguard development environments against a number of supply chain attacks. (The software also helps) development teams to build a process for vetting open source packages for not only known vulnerabilities, but also for malicious packages.”





















