The financially-motivated malware is a shared object library with sophisticated evasive activities that are “nearly impossible to detect”.
An unusual malware affecting Linux operating systems has been discovered targeting the financial sector in Latin America.
Named Symbiote by the researchers from BlackBerry and Intezer who discovered it, the malware is different in that is not a standalone executable file that has to be run to infect a machine. Rather, it is a shared object library that is loaded into all running processes using LD_PRELOAD (T1574.006) to parasitically infect machines.
The first samples of the malware were found in early 2022, targeting the financial sector in Latin America. Domain names used by the malware indicate the threat actors are currently impersonating Brazilian banks, which suggests that these banks or their customers are potential targets.
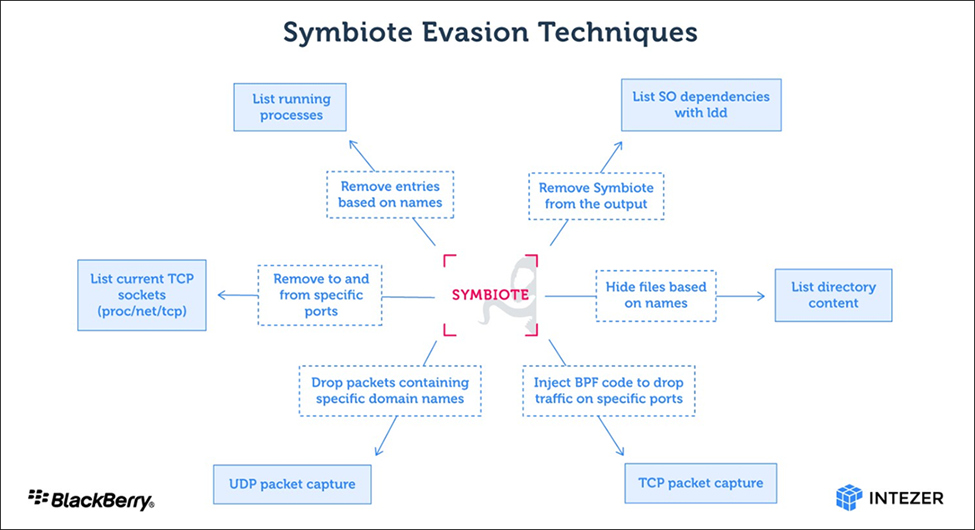
According to the researchers, the main objective of this malware is to capture credentials and to facilitate backdoor access to a victim’s machine. It uses a variety of sophisticated bytecode to hide itself and other files related to malware likely deployed with it—by scrubbing their filenames from any processes and network traffic that could trigger detection. Once it has thoroughly embedded itself into target machines, Symbiote also makes use of rootkit functionality.
In addition to providing threat actors with the ability to remotely access victim machines, Symbiote also allows the attacker to perform automatic credential harvesting.
Symbiote has been described by the researchers as one of the most sophisticated Linux threats they have seen in recent times, and points to the possibility of more such evasive threats ahead as attackers increasingly focus their attention on cloud servers and workloads.
Researchers note that Symbiote’s activities can be detected through network telemetry to detect anomalous DNS requests. In general, security tools such as antivirus and endpoint detection and response should be statically linked to ensure they are not infected by userland rootkits.