Call it whatever you like, but the panicked implementation of mass remote-working is causing a frenzy among cybersecurity experts.
A recent McAfeeLabs blog post has, like many other cybersecurity specialists, highlighted the dangers of mass remote-working.
Around the world, social distancing restrictions came into effect very rapidly, giving organizations little time to prepare for securely managing their workforce remotely. It is important that organizations continue to do business during this tough time, but they must also do it securely to prevent an attack such as ransomware.
From McAfeeLabs’ point of view, protecting organizations in this current climate must be approached from two perspectives: Know your environment and users, then Know your business and real threats.
Know your environment and users
It is important to understand the architecture and technologies being used by employees within your business environment. This gives you visibility into your potential exposure based on vulnerabilities being actively exploited by threat actors so that you can protect your remote workers and business infrastructure/assets.
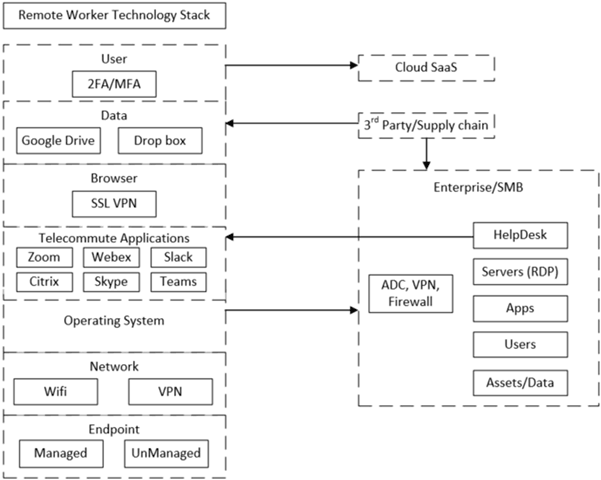
Know your business and real threats
- Adversary Opportunities
Adversaries need an initial access vector to gain a foothold within an organization. They will typically seek out corporate usernames and passwords using techniques enumerated in MITRE ATT&CK, such as phishing or remote exploitation of software vulnerabilities. The telecommuting technology increases the attack surface significantly and is being exploited/researched as evident below:- In 2019, vulnerabilities in Palo Alto Networks, Fortinet, Pulse Secure, and Citrix VPN servers were targeted
- Proof-of-concept exploits have been developed for Citrix NetScaler/Application Delivery Controller (ADC), Cisco VPN routers and the Zoho ManageEngine Desktop Central
- Fox-IT discovered bypassing of a VPN two-factor authentication
- Proof-of-Concept exploits have been developed for vulnerabilities in telecommuting applications such as Zoom, Confluence and Slack
- There have been vulnerabilities recently disclosed in Android and iOS free VPNs
- Remote Desktop Protocol vulnerabilities have been disclosed over the last year such as Dejablue, Bluegate and a proof-of-concept exploit in the case of Bluekeep (wormable)
- In 2019, vulnerabilities in Palo Alto Networks, Fortinet, Pulse Secure, and Citrix VPN servers were targeted
- Controls
- Minimum technical controls for remote worker machines:
- Secure configuration and strong passwords to prevent router compromise
- Keep all software layers patched, VPNs and telecommuter applications
- Do not reuse passwords across personal and work systems
- Robust endpoint security software
- Minimum technical controls for enterprise/SMBs:
- Security hygiene best practices
- MFA/2FA and logging for VPN accounts
- VPN patching
- Secure RDP access
- Segmentation of critical business assets
- Data backups
- User and device identity for employees and 3rd parties/suppliers
- Policies
- Data loss prevention
- Strong passwords
- SaaS security
- Managed vs unmanaged device access
- Training
- Phishing and social engineering training based on the current climate context—“verify before trusting”
- Keep employees informed of phishing campaigns relative to your environment and business
According to the blog post, strong technical controls are a must to protect remote-working teams in the current climate, and there is also no substitute for employee phishing and social engineering training as a successful phish can negate technical controls.
Even multi-factor and second-factor authentication can be bypassed in some cases (using advanced phishing or other techniques) so businesses must all stay vigilant, starting with every employee, in order to protect the entire organizations via a “verify before trusting” approach.





















