The ransomware first locks up their files, then purports that the FBI is penalizing them for their indiscretions!
A new variant of Android malware called Black Rose Lucy has been reported on the Android platform.
When downloaded, the new variant encrypts files on the infected device and displays a ransom note in the browser window that claims an official message from the United States Federal Bureau of Investigations.
The ransom note accuses the victim of possessing pornographic content on their device, stating that the user’s details have been uploaded to the FBI Cyber Crime Department’s Data Center, accompanied by a list of legal offenses that the user is accused of committing.
The victim is instructed to pay a US$500 ‘fine’ via credit card to make the situation go away, unlike the more typical mobile ransomware payout demanded in Bitcoin.
First discovered by Check Point researchers in September 2018, Lucy is a Malware-as-a-Service dropper that originated in Russia. Researchers have collected 80 samples of the new Black Rose Lucy variant. The samples were disguised as harmless-looking video player applications, leveraging Android’s accessibility service to install their payload without any user interaction, creating an interesting self-protection mechanism.
How Lucy works
Lucy leverages a cunning method to slip inside Android devices, giving it the title of “the Achilles Heel in Android’s defensive armor”. Lucy’s order of operations are as follows:
- Lucy is downloaded and installed via social media and instant messenger as a video player application.
- Lucy tricks the user to allow accessibility service by pretending to enable a bogus service, VSO – Video Streaming Optimizer.
- Lucy grants itself administrative privileges by using accessibility service.
- Lucy encrypts the files on the device, storing the encryption key in the shared preferences.
- Lucy displays a ransom note “fine” from the FBI, demanding credit card info to pay it.
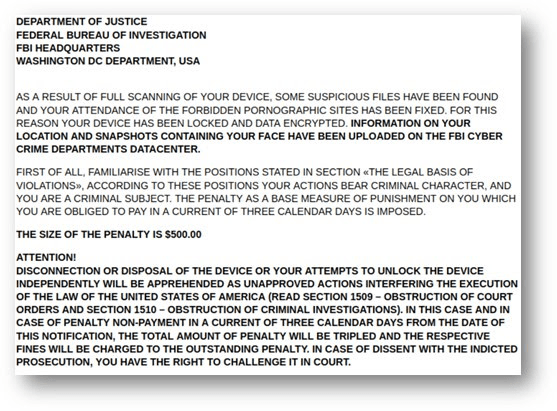
The ransom note
The ransom note purports to be an official message from the FBI and accuses the victim of possessing pornographic content on his device. As a result, all content on the device is encrypted and locked.
In addition, the message states that the victim’s details are now uploaded to the FBI Cyber Crime Departments Data Center, accompanied by a list of legal offenses that the victim is accused of committing. Eventually, the victim is instructed to pay a US$500 “fine” via credit-card.
Aviran Hazum, Manager, Mobile Research, Check Point Software Technologies, said: “To stay safe, I’d install a security solution and only use official app markets. And as always, keep your device’s OS and apps up to date at all times.”