Dubbed a ‘double dragon’ group due to its dual objectives, APT41 is history, at least until more state-sponsored groups replace them!
With the announcement of charges and arrests by the United States Department Of Justice in regard to the notorious APT41 and its computer intrusion campaign tied to the Chinese government, it is now GAME OVER for one of too many more advanced persistent threats and state-sponsored groups that remain at play.
What is APT41? According to John Hultquist, Senior Director of Analysis, Mandiant Threat Intelligence, this group has been the most prolific Chinese threat actor he has tracked over the last year.
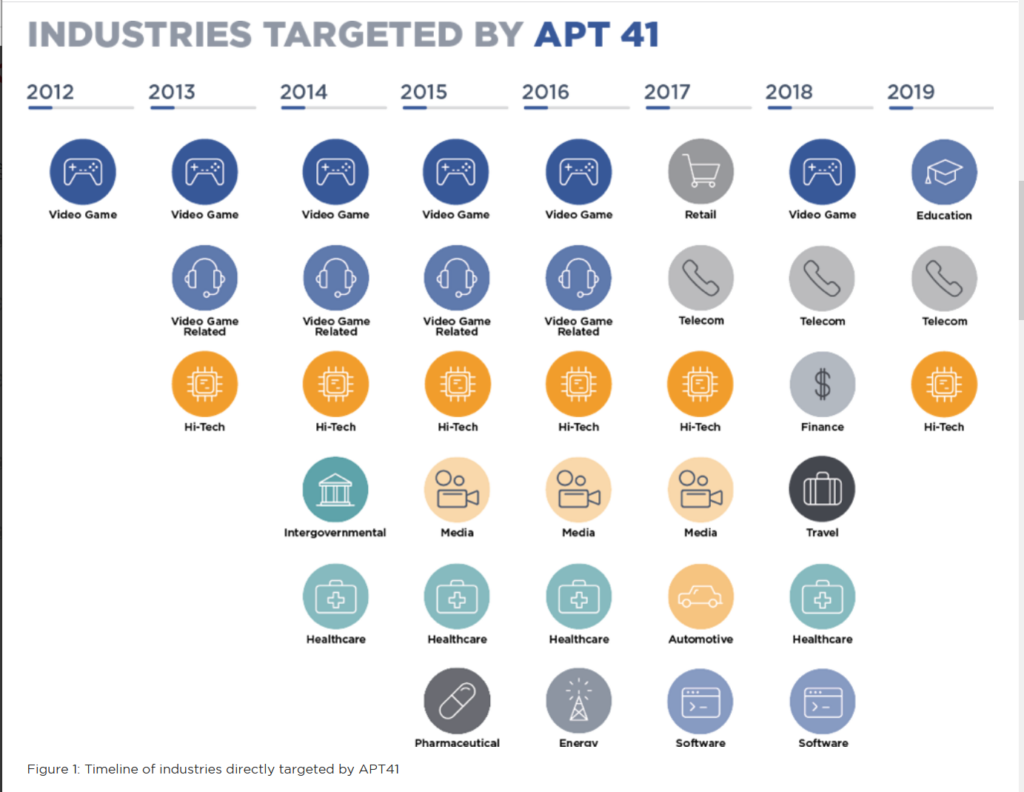
“This is a unique actor, that carries out global cyber espionage while simultaneously pursuing a criminal venture. Their activity traces back to 2012 when individual members of APT41 conducted primarily financially-motivated operations focused on the video game industry, before expanding into traditional espionage, most likely directed by their State. APT41’s ability to successfully blend their criminal and espionage operations is remarkable.”

The double dragons of China
For the record, APT41 has been involved in several high-profile supply chain incidents where they often blended their criminal interest in video games with the espionage operations they were carrying out. For instance, they compromised video game distributors to proliferate malware that could then be used for follow-up operations. They have also been connected to well-known incidents involving Netsarang and ASUS device software updates.
In recent years the group focused heavily on the telecommunications, travel, and hospitality sectors, which are probably attempts to identify, monitor, and track individuals of interest. They have also participated in efforts to monitor Hong Kong during recent democracy protests.
Hultquist continued: “Though much of the intellectual property theft connected to this APT has declined in favor of other operations in recent years, they have continued to target medical institutions, suggesting they may still have an interest in medical technology.”
According to this expert, intelligence services leverage cyber criminals such as APT41 for their own ends because the groups offer expedient, cost-effective, and deniable capability. APT41’s criminal operations appear to predate the work they do on behalf of China, and they may have been co-opted by a security service that would have significant influence over them.
“In situations such as this, a bargain can be reached between the (state) service and the operators, wherein the operators enjoy protection in return for offering high-end talent to the service. Furthermore, the service enjoys a measure of deniability when the operators are identified. Arguably, that is the case right now,” Hultquist concluded.