Cybercriminals are pivoting their campaigns around the domain name system, but security awareness is also improving, says a threat report.
In an sudden era of remote-working and heavy dependence on connected devices, company networks suddenly become more complex, resulting in a greater risk of cyber-attacks, especially those targeting the Domain Name System (DNS). DNS attacks can halt traffic, lead to data theft or prevent users from accessing critical apps.
Cybercriminals have been zooming in on the cloud as more businesses have had to rely on the platform for urgent implementation of remote workforce. Similarly, the awareness of the importance of DNS security has also been on the rise by about 15% compared to the previously, because of increased cyberattacks.
This is what a global study on DNS threats has uncovered, among other trends in the region. Conducted to gain a better understanding of the DNS threat landscape and the measures companies are taking to mitigate cyberattacks, the study by market intelligence firm IDC involved 900 organizations globally across a variety of industries.
Study sponsor EfficientIP has found that 79% of companies experienced at least one attack with an average of 9.5 attacks per company in the study period. The average cost of an attack decreased slightly, from an average number of US$1,070k in 2019’s report to US$924k this year.
The reasons for this could vary, but one possibility is that organizations are recognizing the importance of DNS for their daily operations, and they are starting to secure it more fully.
Next to costs, the report measured six other impact statistics, nearly all of which saw rises from last year’s numbers. Notably, 82% of companies suffered application downtime—both via cloud and in-house. This demonstrates how critical DNS is for ensuring access between users and applications. The cost of attacks for organizations in Singapore had increased from S$294 to S$1,022.
Regional findings
- Attackers appear to increasingly target the cloud. In Asia, 65% of respondents in India experienced cloud service downtime, against the global average of 50%.
- Organizations across all industries suffered an average 9.5 attacks so far this year. This amounted to 10.73 attacks for Singapore, and 12.13 attacks in India, the highest globally, against 10.44 for Asia as a region. These figures illustrate the pivotal role of the DNS for network security, as threat actors made use of DNS’ dual capacity as either a threat vector or a direct objective.
- In-house app downtime remained high: 62% globally this year compared to 63% last year, with Malaysia standing out in Southeast Asia at 66%. As a whole, application downtime—whether in-house or in the cloud—remained the most significant result of DNS attacks.
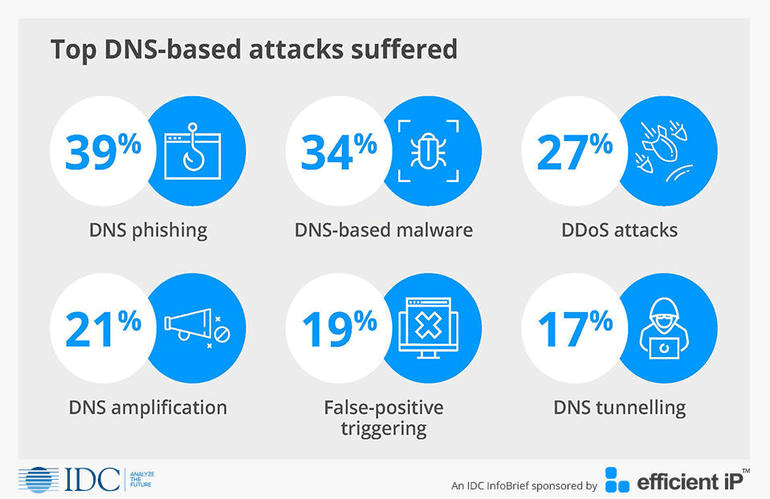
- Phishing led in popularity (39% of companies experienced phishing attempts), followed by malware-based attacks (21%), and traditional DDoS (27%). The size of DDoS attacks was also seen increasing, with almost two-thirds (64%) being over 5Gbit/s. In terms of having sensitive customer information stolen, Singapore scored the highest globally at 30%, outpacing India (27%) and Asia (25%), as well as the global average of 16%.
The other side effects of attacks included cloud service downtime (50%), a compromised website (46%), brand damage (29%), loss of business (29%), and the theft of sensitive information (16%).
According to EfficientIP and IDC, the increased reliance on the cloud during the coronavirus lockdown likely made it a more inviting target for attackers. Going forward, businesses can rely on threat intelligence and user behavioral analytics to enhance attack protection capacity.
Security Operations Centers and Security information and event management (SIEM) software are also useful, with 29% citing SIEM software to detect compromised devices, and 33% passing passed DNS information to SIEM for analysis (up from 22% in 2019).





















