Weeks before the anticipated international shopping event, cyberattackers have already set up spoofing websites and domains, ready for bumper data harvests!
Amazon Prime Day, the e-retail giant’s two-day discount event, is right around the corner, expected to launch on June 21st. Other than shoppers, one other group is also waiting for the event: threat actors and hackers.
In fact, reports from Check Point research show that cybercriminals are already on the field, spreading malicious content and gearing up to leverage their own ‘special deals’ on those two days or beyond.
So far, researchers have found malicious and suspicious domains being erected, that are expected to lure eager online shoppers in various phishing campaigns to steal credentials, and gain unauthorized access to funds and financial transactions.
Alarm over domain registrations
In last year’s Amazon Prime Day in October, 28% of domains registered containing the word “Amazon”, were found to be malicious; another 10% were suspicious. Furthermore, 20% of domains registered containing the words “Amazon” and “Prime” were found to be malicious.
Phishing for victims
This year, in the past 30 days, over 2,303 new Amazon-related domains were registered, compared to 2,137 in 2020. Almost half (46%) of those domains have been found to be malicious and another 32% suspicious. As for new Amazon Prime’s related domains, there were 32% malicious sites.
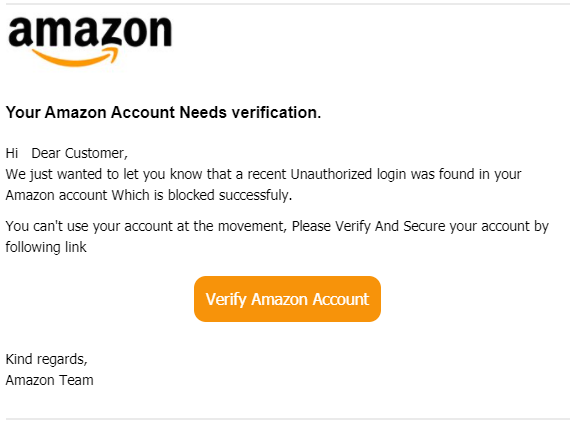
To target Amazon Prime shoppers, attackers set up fake websites that appear to be owned by Amazon or a trusted entity like the victim’s bank, workplace, or university. Via these websites, attackers attempt to collect private information like usernames and passwords, or payment information.
Here is an example of a phishing mail that seems like it was sent from “Customer Service”, but from looking on the email address it is clear that it is not legitimate: (admin@fuseiseikyu-hl[.]jp). The attacker was trying to lure the victim to click on a malicious link, which redirects the user to http://www[.]betoncire[.]es/updating/32080592480922000 – The link is inactive. Subject: Mail sent from Amazon:Wednesday, June 2, 2021 (GMT+10)
From: Customer Service (admin@fuseiseikyu-hl[.]jp)
According to Gary Gardiner, Head of Security Engineering (Asia Pacific and Japan), Check Point Software Technologies: “The danger here is being tricked into giving up your credit card information, your passwords and even your home or email address to cyber criminals. Their goal is to make money off your personal details. The tactic cybercriminals use in for their deception is domain spoofing, where you click on a page that appears to be from Amazon, but you’re actually on malicious ground. Clearly, cybercriminals are doubling-down on Prime Day this year. I strongly urge Prime Day shoppers this year to be extra cautious, to watch for misspellings, and to share only the bare minimum personal information. I would triple check emails in the inbox that allege they’re from Amazon next week.”