The impact of APAC’s AI buildout on cybersecurity in 2026
By Victor Ng | Dec 9, 2025
Is your AI secretly sabotaging your organization?
By Victor Ng | Dec 1, 2025
Lessons learnt from the first reported AI-orchestrated attac...
By Victor Ng | Nov 28, 2025
The new face of fraud in the AI era
By Victor Ng | Nov 25, 2025
Shadow AI – the hidden risk in APAC organizations
By Victor Ng | Nov 24, 2025
SECURITY NEWS
Staying Ahead – RSA Conference
By RSA Conference | Jun 12, 2019
Amrin Amin, Senior Parliamentary Secretary (SPS), Ministry of Home Affairs & Ministry of Health Proliferation of digital...
-

Cybersecurity Futures 2025: Insights and Findings for RSAC
By RSA Conference | May 12, 2019
-

-

The New Why of Cybersecurity
By RSA Conference | Mar 12, 2019
-

Think and act like a hacker to protect your company’s assets
By RSA Conference | Jan 12, 2019
EXPERT OPINIONS
Staying Ahead – RSA Conference
By RSA Conference | Jun 12, 2019
Amrin Amin, Senior Parliamentary Secretary (SPS), Ministry of Home Affairs & Ministry of Health Proliferation of digital...
-

Cybersecurity Futures 2025: Insights and Findings for RSAC
By RSA Conference | May 12, 2019
-

-

The New Why of Cybersecurity
By RSA Conference | Mar 12, 2019
-

Think and act like a hacker to protect your company’s assets
By RSA Conference | Jan 12, 2019
TIPS
Staying Ahead – RSA Conference
By RSA Conference | Jun 12, 2019
Amrin Amin, Senior Parliamentary Secretary (SPS), Ministry of Home Affairs & Ministry of Health Proliferation of digital...
-

Cybersecurity Futures 2025: Insights and Findings for RSAC
By RSA Conference | May 12, 2019
-

-

The New Why of Cybersecurity
By RSA Conference | Mar 12, 2019
-

Think and act like a hacker to protect your company’s assets
By RSA Conference | Jan 12, 2019
Staying Ahead – RSA Conference
By RSA Conference | Jun 12, 2019
Cybersecurity Futures 2025: Insights and Findings for RSAC
By RSA Conference | May 12, 2019
The New Why of Cybersecurity
By RSA Conference | Mar 12, 2019
Infographics

Verizon 2025 Mobile Security Index Repor... Infographic

7 themes shaping security and identity i... Infographic

Phishing trends in Q3 2024 Infographic

Sumsub’s First Global Fraud Index ... Infographic

Verizon 2024 Mobile Security Index Infographic

Acronis Cyberthreats Report H1 2024 Infographic

Verizon 2024 Data Breach Investigations ... Infographic

2024 Global Threat Report Infographic


APJ 2023 Direction of Technology Report Infographic

Trust and collaboration to fight fraud i... Infographic

State of Cybersecurity in ASEAN 2023 Infographic


Use of phishing kits surged by 25% in 20... Infographic

2023 Global State of Cybersecurity Infographic

Unit 42 Cloud Threat Report Infographic

Know your adversaries Infographic

Usher in the Year of the Rabbit, not the... Infographic

APAC cybersecurity predictions 2023 Infographic

#ShopSafe tips for your customers this h... Infographic

Infographics: 6 steps to defend against ... Infographic

10 best practices to turbo boost cyberse... Infographic

Tips: Ways to implement risk-based vulne... Infographic

2022 State of Access Control Infographic

Anatomy of a multiple-gang attack Infographic

Infographics: Cyber Threat Landscape in ... Infographic

Ransomware: true cost to business 2022 Infographic

Q1 2022 ransomware update Infographic

Simpler and stronger multi-device passwo... Infographic

Charity scams in 2022 Infographic

Ransomware gold rush Infographic

Balancing risk and reward Infographic

State of Cybersecurity Report ASEAN 2022 Infographic

10 trends that will shape the fraud land... Infographic

Top trends in data protection for 2022 Infographic


Fighting financial crimes in 2022 Infographic

2022: How APAC is preparing for a new th... Infographic
APAC security predictions 2022 Infographic

Global Security Attitude Survey 2021 Infographic
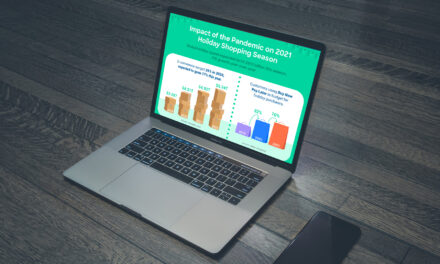
Impact of pandemic on 2021 holiday shopp... Infographic

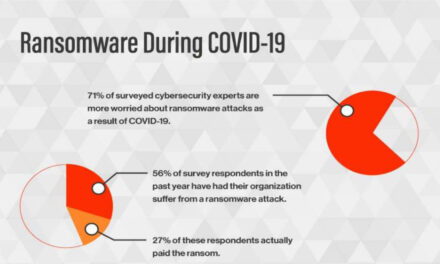
Ransomware attackers don’t take holidays... Infographic

Redefining trust and risk in APAC Infographic

Patch management challenges Infographic

2021 State of PKI Automation in APAC Infographic

Asia Pacific SMBs prepare for digital de... Infographic

Rethink your SMS approach Infographic

How companies tackle trade compliance Infographic

Security risks of network overprovisioni... Infographic

2021 Global Incident Response Threat Rep... Infographic

Top email and social media phishing subj... Infographic


2021 Thales Data Threat Report Infographic

APAC security budgets and priorities 202... Infographic
Global security insights 2021 Infographic
Is your fraud protection turning away cu... Infographic

Mobile Application Security report: Peri... Infographic


The CISO view on zero trust Infographic

Impact, costs and benefits of modern dat... Infographic
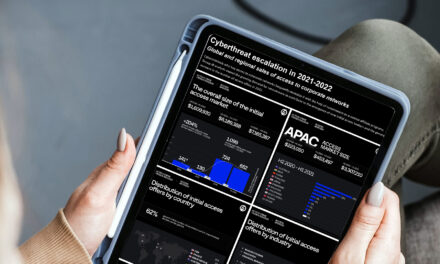
Big game hunting, ransomware dominate cy... Infographic
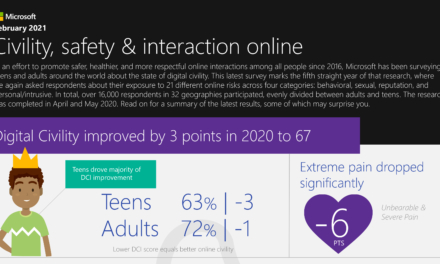
Civility, safety and interactions online Infographic

Top phishing email subjects Infographic


Looking back: 2020 cyberthreats Infographic

6 cybersecurity predictions for 2021 to ... Infographic

5 ways to combat fraud during the holida... Infographic

Growing need to secure cloud privileged ... Infographic
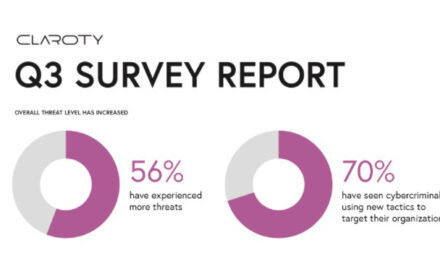

2020 Cost of a Data Breach Report Infographic

Authentication vs authorization Infographic

Asia Pacific Security Endpoint Threat Re... Infographic

2020 open source security and risk analy... Infographic

Is it time to reinvent cybersecurity? Infographic

Prevalent malware exploiting COVID-19 Infographic

Backup and storage through the ages Infographic

Are APAC businesses ready for their tran... Infographic

5 predictions for digital payments in 20... Infographic

APAC organizations’ misplaced confidence... Infographic
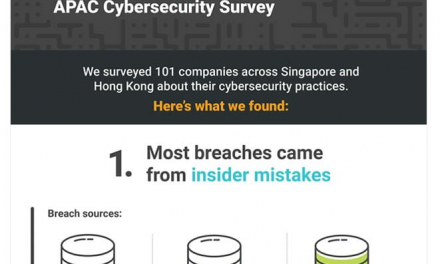
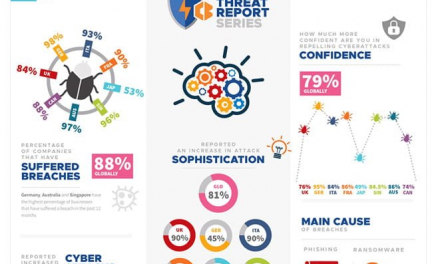
Carbon Black Global Threat Report Infographic

2019 State of Enterprise Secure Access Infographic

A Look Back at the First Year of GDPR Infographic
Case Studies
Bangladesh LGED modernizes communication while addressing data security concerns
By CybersecAsia editors | Dec 5, 2025 | Case Study, News
To meet emerging data localization/privacy regulations, the government engineering agency deploys a secure, unified digital platform supporting 6,000 users nationwide.
-

-

Meeting the business resilience challenges of digital transformation
By Victor Ng | Nov 12, 2025 | Case Study, News, Newsletter
Whitepapers
Closing the Gap in Email Security:How To Stop The 7 Most SinisterAI-Powered Phishing Threats
By Securonix | Nov 26, 2025 | Sponsored, Whitepapers
Insider threats continue to be a major cybersecurity risk in 2024. Explore more insights on trends, challenges, and solutions by downloading the 2024 Insider Threat Report and discover how to stay ahead of evolving risks!
-

2024 Insider Threat Report: Trends, Challenges, and Solutions
By Securonix | Jan 16, 2025 | Sponsored, Whitepapers
-

AI-Powered Cyber Ops: Redefining Cloud Security for 2025
By Securonix | Jan 16, 2025 | Sponsored, Whitepapers
-

Data Management in the Age of Cloud and AI
By Rubrik | Nov 8, 2024 | Case Study, Sponsored, Whitepapers