How one city bolstered its data protection laws to stop the multiplier effect of lax data-breach vigilance and incident reporting.
While 2020 was a difficult year for most organizations, massive surges in data breaches could have had a multiplier effect on victims whose identity credentials had been exploited for even more cyberattacks.
Such a domino effect cannot be allowed to proliferate amid global economic tensions, even if the measures to curb it will add to the financial burden of organizations that may be at the brink of collapse.
Amid the digital chaos, it certainly is not cheap to tighten cybersecurity postures and quickly own up to being a victim of a hacking incident, because it can affect brand image and reputation at the worst possible time.
Arguably, organizations can delay disclosure to buy time to perform many ‘tweaks’ to the statistics when they finally own up. And that is just the tip of the iceberg where increasing the time-to-disclosure is concerned.
The 2020 identity breach statistics
First, a preamble: For the third consecutive year, unauthorized account access was the leading cause of data breaches worldwide, increasing year-over-year for the past two years, and accounting for 43% of all cybersecurity incidents last year, according to a recent study on consumer identity breaches.
This constituted an unprecedented 450% surge in the theft of usernames and passwords globally for use in many other cybercriminal activities—as far as data from a Jan-to-Dec study last year of consumers across the USA, the UK, Germany, Australia and Singapore is concerned.
According to Ajay Biyani, Regional Vice President (ASEAN) of ForgeRock, which commissioned the study: “To address these increased risks, organizations need to make use of AI and machine learning (ML) technologies to spot abnormal behavior and institute policies that ensure accurate identity access. A modern hybrid Identity and Access Management (IAM) system should be implemented to ensure that adequate protections exist both in on-premises environments and in the Cloud.”
For the only Asian country covered by the study, Biyani noted that the Singaporean government’s move to make data breach reporting mandatory comes “at a crucial time and will be pivotal to ensuring businesses can identify weak points in their online experiences that may otherwise lead to cyberattacks for both employees and customers.”
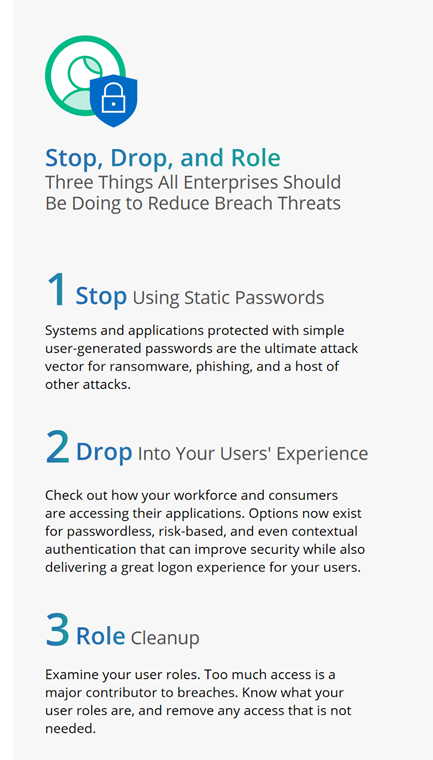
Are passwords passé?
In the study’s sample population, breaches affecting the smaller enterprises (but with many breaches still involving tens of millions of records) saw the biggest surge with a 50% increase. This could indicate that even smaller enterprises cannot afford to put off adopting a Zero Trust posture.
Again, unauthorized access continues to be the leading cause of breaches in this case. Questionable yet common security lapses, like sharing or reusing passwords, gave bad actors an easy path to gaining access to personally identifiable information (PII) such as date of birth and national identity card information, which was found in one-third of all breaches.
Argued Fran Rosch, CEO, ForgeRock: “For too long, usernames and passwords have been the backbone of providing people secure access to their digital lives. The findings in our identity breach report reveal that it’s time for change. The surge in breaches involving usernames and passwords at 450% clearly emphasizes the need to adopt a strong digital identity and access management solution that offers the ability to go passwordless. It also gives companies a much better chance at reducing data exposure, as well as lowering their reputational and financial risk.”
Zooming in on the little red dot
Over in the tiny island of Singapore—which nevertheless is one of the most connected and technologically adaptive countries in the world, the banking sector saw a 20-fold increase in phishing scams in H1 2020.
On average, 28% of residents there reported they had suffered at least one cybersecurity lapse during the year, while the organizations targeted tended to be small- and medium-sized enterprises. The most heavily impacted industries throughout 2020 were banking, healthcare, retail and manufacturing. Compared to all of 2019, ransomware attacks had risen by a reported 75% in the first 10 months.
According to the Cyber Security Agency (CSA) of Singapore, the biggest breaches in Singapore were due to lapses in cybersecurity practices and technology and led to the disclosure of up to millions of records. A misconfiguration at an electronics and gaming hardware vendor in Singapore led to the disclosure of approximately 100,000 records, while unauthorized access at an online shopping service resulted in five million records being subject to unauthorized access.
Were the numerous incidents reported in a ‘timely’ manner as deemed by the CSA? Apparently not, not least because the data privacy and protection regulations of 2012 were not explicit and exhaustive enough, thereby leading to loose interpretations and/or exploitations of loopholes.
In response, the city has since Feb 2021 revised its personal data privacy and protection guidelines to address the non-negotiable and urgent nature of data breach reporting henceforth:
- Organizations must henceforth notify the authorities of any data breach involving personal data of 500 or more individuals. Affected individuals must be notified if the data breach is likely to result in significant harm to them. The Personal Data Protection (Notification of Data Breaches) Regulations 2021 provide a prescribed list of personal data or classes of personal data that shall be deemed to result in significant harm to affected individuals if compromised in a data breach.
- Notifications to the data protection authority (the Personal Data Protection Commission) must be made as soon as is practicable, but in any case no later than three calendar days after the day the organization makes the assessment that a data breach is a notifiable data breach. Notifications to individuals must be made as soon as practicable, at the same time or after notifying the Commission.
Until the revision, the Singapore government had already made the penalty cost of any breach massive through heavy fines and legal proceedings, which are superimposed over the financial and reputational losses. With the February revisions, the Singapore authorities have issued clear writing on the wall to organizations: take cybersecurity seriously and report data breaches in a transparent, clear and expeditious manner or face the heavy consequences.
Biyani commented: “We support the Singaporean government’s move to make data breach reporting mandatory this year, it is coming at a crucial time and will be pivotal to ensuring businesses can identify weak points in their online experiences that may otherwise lead to cyberattacks for both employees and customers.”
Ultimately, while it may be a tough act to beat cybercriminal and state-sponsored cybercriminals, the real point of revising data protection regulations is to control the damage when breaches happen, so that the huge volume of victims does not add to an even wider and costlier casualty list long after the initial breach.
For that to happen, organizations are now expected to report breaches without delay (because damage reports can be ‘window-dressed’, and these take time), and without any delays that can cascade into greater longer-term damage to multitudes of corporate and private victims worldwide.




















