Network security in the cloud era featured in a big way among experts and enterprise end-users at Aruba Atmosphere 2022
As-a-service solutions are going through a global boom, coupled with the proliferation of hybrid work environments, the annual Aruba Atmosphere Conference – SEATH and India – held in Bangkok, Thailand in September 2022, gathered business-driven companies from the region to discuss and dive into the best industry practices and to hone new skills that will help to continuously modernize their networks.
“With the new normal being defined by hybrid cloud strategies, emerging IoT environments and remote work, achieving connectivity is key in today’s disconnected world,” said Steve Wood, Vice President, APJ at Aruba, a Hewlett Packard Enterprise company.
“We know that making connections anywhere, anytime has become imperative now more than ever, and with a focus on network modernization, enterprises that prioritize digital transformation and acceleration will be able to address the tough challenges that come with network orchestration, management and security to eventually drive business growth.”
The event was centered around three key technology principles – agility, automation and security. According to David Hughes, Chief Product and Technology Officer, HPE Aruba, enterprise customers are asking for three things in the increasingly complex cloud era:
- A broad portfolio of solutions managed through one common platform
- A secure network that can predict and fix problems before they happen
- A more adaptive model that can flex with their business
In the first place, what is driving the need for network modernization? Hughes highlighted the following trends:
- Hybrid work
- DX acceleration
- Personalized experiences
- Need for efficiencies
Static networks no longer meet growing business demands or support changing security requirements. As enterprises embark on digital transformation initiatives and adapt to hybrid work environments, they see the need to adopt a modern network architecture, for a seamless and secure connection to facilitate their core business functions from anywhere.
Hughes said: “We hear customers telling us they want a very broad set of solutions – with one uniform way to manage them. They also want to be able to take all the data collected and use machine learning for recommendations to predict and fix problems, as well as a more adaptive model for business flexibility.”
Aruba’s answer to meeting these needs: the Edge Services Platform (ESP):
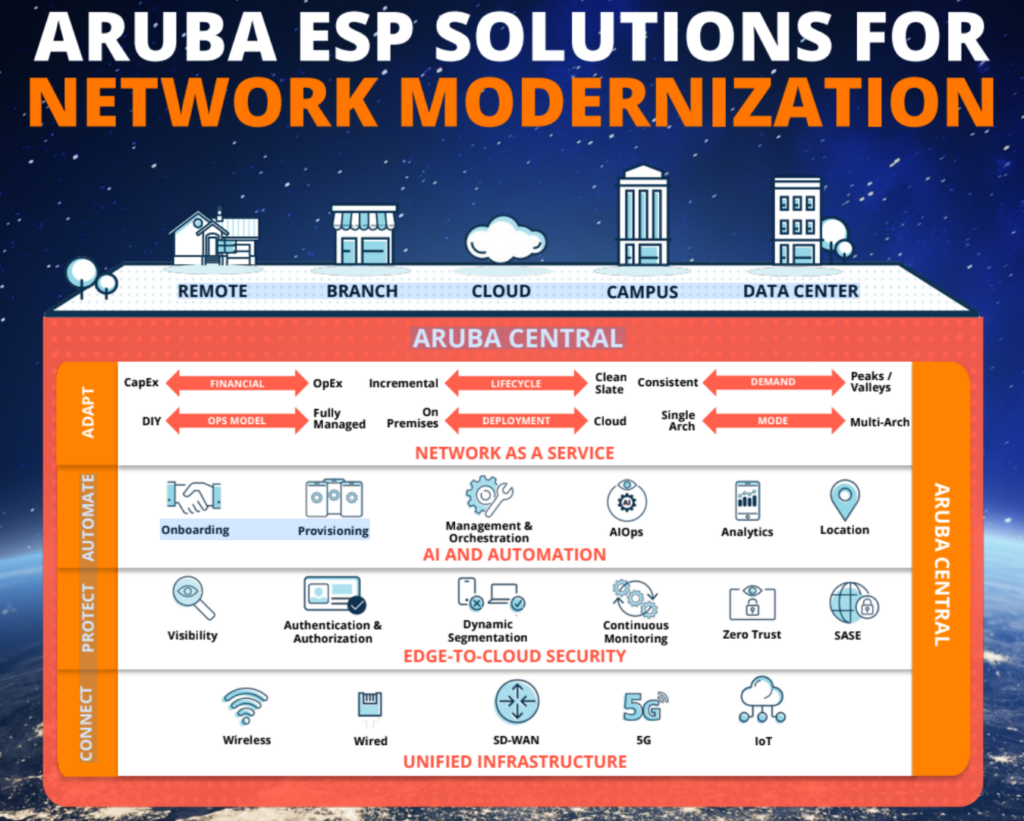
What is needed for network modernization
Experts including Hughes and Carlos Gomez Gallego, Chief Technology Officer, APJ, HPE Aruba expounded on how network modernization in hybrid multi-cloud environments can be achieved:
- Agility to adapt to fast-changing business requirements: The increasing ease in adopting network-as-a-service (NaaS), to drive future-ready unified, cloud-native, standards-based architecture and optimize budget and staffing resources.
- Automation to supplement limited human resources: Achieving simplified workflows and AI-powered automation to reduce time and resources required to plan, deploy, and manage networks that support remote, branch, campus, and cloud connectivity.
- Security based on zero trust principles: Importance of threat detection and protection by tapping zero trust and SASE frameworks for edge-to-cloud security, utilizing built-in identity-based access control, and dynamic segmentation to contain and mitigate the impact of a breach.
Aruba customers also shared their experience at the event.
“We had to drive a high-level digital transformation initiative in Asia Pacific and aimed to build a zero trust network to maximize cloud utilization and strengthen IT infrastructure and security,” said Irwan Yulianto, GM of IT at Panasonic. “Our network required a modern, agile network architecture, and our legacy MPLS network was not viable to spearhead change.”
“Our deployment of the Aruba EdgeConnect SD-WAN solution has become a key enabler of our digital journey, building the foundation of our zero trust network and empowering us to ensure always-on performance from the edge to the cloud. We now have complete, single-pane, network visibility for ease of management and we are certainly on our way to realizing the full promise of the cloud.”
Sunti Medhavikul, Managing Director at UIH, said: “As a leading managed service provider in Thailand, our customers cover all industries including core infrastructure providers. It is instrumental that we are able to empower our geographically distributed customers with a high-performing solution.”
“Automation sits at the heart of our tech partnership consideration as we manage our customers’ complex network requirements,” added Sunti. “Deploying the cloud-native Aruba Central management platform was key in our customers’ digital projects as it could effectively scale very large and distributed networks. With our technology partnership with Aruba, we have the ability today to modernize our customers’ networks with strict adherence to service level agreements and grow with them.”
Securing the modern network
Aruba’s APJ CTO Gallego emphasized the need for security to scale with the hybrid multi-cloud environments we operate in today. With the biggest vulnerability being the human factor, a single platform for a single source of truth and simplified management is very important.
“It’s not just about the security that we have inside the Aruba ESP, but the integration that we also have with our security partners, to orchestrate for a whole variety of other security use cases. The more tightly that we can integrate the networking and security capabilities of Aruba with our partners, the less room there is for error, and for vulnerabilities.”
Zero trust and role-based access are a big help in ensuring humans are brought in to strengthen, not weaken, network security.
Gallego added: “Zero trust is really resonating with customers and partners around the world. And I think one of the reasons is because when there are cybersecurity incidents, it is much more visible to the general public now than it previously was. The awareness is much higher, and it’s critical to have that awareness because we need all our employees to be part of the solution, not part of the problem. And the more awareness that everybody has about the importance of cybersecurity, the more we can minimize that human element risk to organizations.”
He explained that zero trust is a framework on resilient networks are built. It involves designing networking products with security built in.
Unlike wired networks, which require the user to plug in a cable into a port, wireless connections just need a password. Therefore, it becomes critical that the network is designed and built with the capability to identify every user, whether an endpoint, a network, an app or a device – and decide what level of access should be granted based on the role each endpoint is playing at any specific time.
“Our research in Development and Engineering is all about providing zero trust, regardless of whether you’re connecting via wireless or wired, remotely or via hybrid work. We need to provide that same security experience in the office, out of the office, and independent of the connectivity type,” said Gallego.
Observability is very important, so we can detect any anomaly in what a device or user is doing.
“Observability is based on visibility. Visibility is the starting point. Observability is ongoing monitoring and adopting behavior analysis to make sure that everything is operating as intended. The ‘intelligent edge’ is what makes observability possible. When we refer to the intelligent edge, I’m talking about predictive. One of the other key components for us is working with our security partners. The more context, the more intelligence that we can gather from either observing ourselves or from the data that comes from our partners, the more intelligent decisions that we can make, to keep the network and users and devices secure.”
The intelligent edge is where humans and machines interact. At the point of connection, if we can apply as many security controls, we can minimize the attack surface, and the possibility for vulnerabilities to be introduced into the network. Data gathered at the intelligent edge can be used by AI/ML to help other organizations and users block potential threats at the edge.
Finally, segmentation of traffic is also important to contain and control damage, in the event of a successful breach.





















