With more hackers stealing password hashes from single sign-on terminals, it is time to employ access management best practices.
New global research—across the U.S., Canada, U.K., Germany, France, Australia and New Zealand, Singapore and Hong Kong—has revealed the significant prevalence and impact of cyberattacks that use stolen hashed administrator credentials, also referred to as Pass the Hash (PtH) attacks, within businesses.
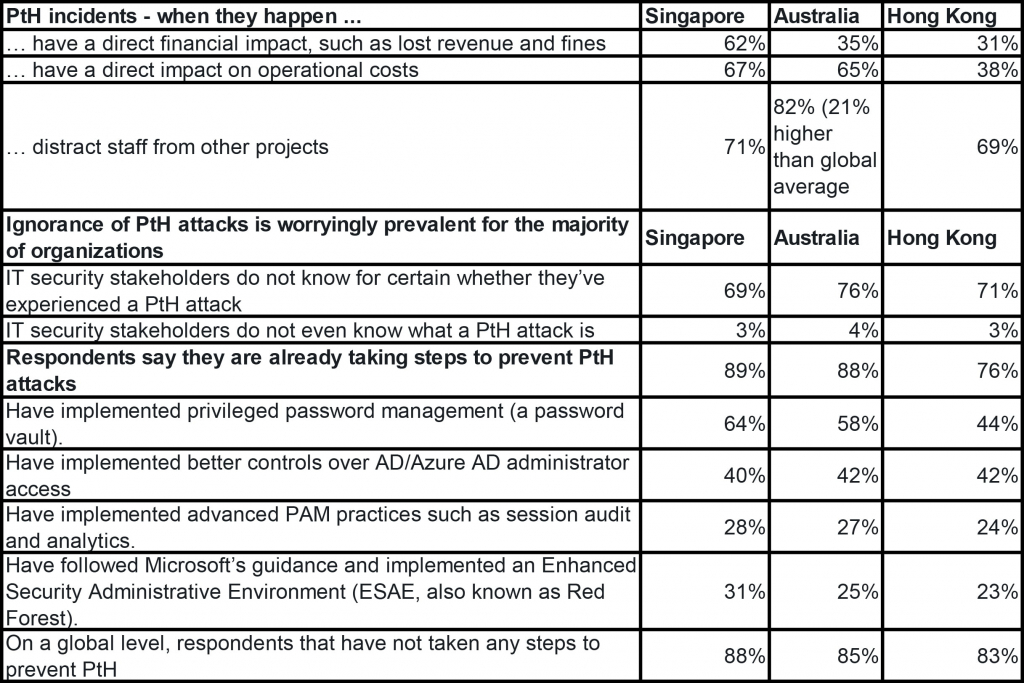
Among the survey’s most noteworthy findings is that 100% of Australian respondents say that PtH attacks, when they happen, have a direct business impact on their organization. The survey shows that 92% of respondents in Hong Kong, and 100% in Singapore, whose company experienced a PtH attack reported that PtH attacks have had a direct business impact on their organizations.
The “2019 State of Identity and Access Management” study by One Identity, conducted by Dimensional Research, polled more than 1,000 IT professionals globally from midsize to large enterprises and who held responsibility for security and who are very knowledgeable about IAM and privileged accounts about relevant cyberattack experiences, trends and approaches to Identity Governance and Administration (IGA), privileged access management (PAM) and Identity SaaS.
The results reinforce the crucial need for organizations to deploy effective Active Directory (AD) management and privileged access management solutions and practices, given that PtH attacks primarily result in unauthorized use of privileged credentials to compromise enterprise systems and data.
How is PtH perpetrated?
In a typical PtH attack, an attacker obtains privileged credentials by compromising an end-user’s machine and simulates an IT problem so that a privileged account holder will log into an administrative system. Those login credentials are stored as a hash that the attacker extracts and uses to access additional IT resources across the organization. Without a holistic and strategic approach to protect privileged accounts and identify when privileged access is being abused, a cybercriminal leveraging a PtH technique can gain access to an entire network, rendering all other security safeguards ineffective.
According the survey, IT security stakeholders recognize the damage PtH attacks can cause, however, many are still not implementing the most important measures available to fight them. Additional findings from the report include:
According to Darrell Long, vice president of product management, One Identity: “The results of the 2019 survey indicate that despite the fact that Pass the Hash attacks are having significant financial and operational impact on organizations, there is vast room for improvement in the steps organizations are taking to address them. Without a holistic and strategic approach to protect privileged accounts and identify privileged access abuse, organizations could very well leave their entire network exposed to cybercriminals leveraging the PtH technique, with detrimental repercussions to the business.
Significance to Australia
The survey shows that Australian businesses need to be vigilant in the face of the growing threat of Pass the Hash attacks given the significant effect they are having on companies’ bottom-lines and day-to-day operations. According to Long, while Australian businesses are taking steps to protect themselves, it is worrying that the vast majority cannot definitively state if they have been a victim of such an attack. This is partly due to the sophisticated nature of today’s cyber-attackers who are circumventing robust security systems. Such was evident in the recent case where hackers accessed private student information from one of Australia’s major university networks in a manner that was described by the University as a state-of-the-art hack, carried out by an actor at the very top of their game and at the very cutting edge.
Significance to Hong Kong
According to Serkan Cetin, Technical Director, APJ, One Identity: “While organizations in Hong Kong have taken steps to mitigate the risk of Pass the Hash data breaches, there is still a startling number who have not implemented any sort of plan to address the risks that these breaches may bring. With the number of data breaches in Hong Kong reaching a record high in 2018, a robust identity-centric strategy to secure privileged credentials needs to be a priority for organizations to prevent them from falling into the wrong hands.”
Significance to Singapore
According to Serkan, the results of the survey indicate that Pass the Hash attacks are disruptive to organizations, with all respondents in Singapore reporting some sort of impact to their organization due to unauthorized access to sensitive information. While organizations in Singapore have taken steps to mitigate the risk of Pass the Hash data breaches, there is still a startling number who have not implemented any sort of plan to address the risks that these breaches may bring. “The recent SingHealth data breach is a high-profile example when unauthorized access to confidential data occurs, and this shows that a robust identity-centric strategy to secure privileged credentials needs to be a priority for organizations to prevent these details from falling into the wrong hands.”
Takeways from the survey
Effective PAM and AD-focused identity and access management (IAM) are critical components in any organizations’ security strategy; but the 2019 State of Identity and Access Management study shows businesses are still struggling to implement best practices.
Steps to eliminate IAM and PAM challenges include controlling and automating AD permissions to protect the directory by constantly evaluating administrator permissions and proxying changes on behalf of the administrator, and enabling delegation of exactly the right permission at a much more granular level than native tools. Best practices would combine a secure and hardened password safe, session management and monitoring, and threat detection and analytics to help organizations securely store, manage, record and analyze privileged access.





















