You will need a python, a blue tooth, and a raspberry pie … among other handy gadget thingeys.
The convenience of keyless entry systems is a nice to have. Just be within the proximity of your vehicle and the doors are automatically unlocked.
However, such convenience can come at a price: security. One example that was made public in November 2020 was a set of vulnerabilities in the Tesla Model X keyless entry system discovered by Lennert Wouters at the University of Leuven in Belgium.
So, yes: Automotive keyless entry systems can be broken into, given the right tools. With more cars featuring connectivity features for convenience and luxury, the attack surface has increased in turn.
Interested to know how car thieves do it, and what manufactures need to shore up to defend against sophisticated attackers? According to Dr Dennis Kengo Oka, Principal Automotive Security Strategist, Synopsys Software Integrity Group, the Tesla Model X was hacked as follows …
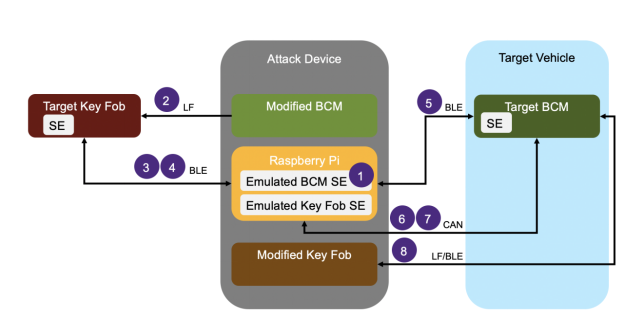
- Step 1 (Equipment preparation)
The attacker uses a pre-prepared attack device consisting of a modified body control module (BCM), a modified key fob, and a Raspberry Pi. Modifications include replacing the Secure Element (SE) chip with Python scripts running on the Raspberry Pi that emulate the SE. - Step 2 (Using Bluetooth trickery)
The attacker approaches the target vehicle, reads the unique vehicle identification number (VIN) through the windshield, and configures the emulated SE for the modified BCM in the attack device to use the target VIN. Using an identifier derived from the VIN, the attacker forces the previously-paired target key fob to advertise as connectable over Bluetooth Low Energy (BLE). - Step 3 (Injecting malicious firmware)
The attacker pushes a malicious firmware update over BLE from the Raspberry Pi to the target key fob in order to gain full control of the key fob. After the target key fob has been updated, the attack device reconnects over BLE. The attacker is now able to extract a number of valid one-time unlock commands (e.g., unlock door, trunk, etc.) for the target vehicle from the SE in the key fob. - Step 4 (Gaining physical entry)
The attacker approaches the target vehicle and uses the valid unlock commands to unlock the target vehicle. The unlock commands are sent over BLE from the Raspberry Pi to the target BCM. Once inside the vehicle, the attacker can physically connect the attack device to the in-vehicle network over the diagnostics port located below the central display. The attack device connects to the target BCM over controller area network (CAN). The attack device instructs the target BCM to pair with the modified key fob. After passing a challenge-response authentication with the BCM to add the modified key fob, the necessary credentials are stored in the emulated SE for the key fob.
- Step 5 (Gaining engine control)
The attacker starts the vehicle using the newly-paired key fob on the attack device to successfully perform a challenge-response authentication using the previously stored credentials in the emulated key fob SE. Game over.
Key system weaknesses
The two main vulnerabilities/weaknesses that allow such attacks are summarized in Table 1.
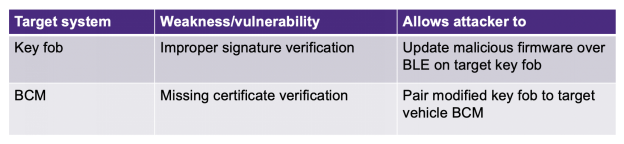
Firstly, although the car’s key fob performs signature verification, the hackers found a vulnerability that allows the use of BLE to update the key fob with malicious firmware.
Secondly, although valid key fobs typically store signed certificates received from the back end and those acquired during provision, these certificates are not verified by the vehicle BCM while pairing with the key fob.
A signal to buck up
New cyber security engineering standards for road vehicles called ISO SAE 214342 and regulations such as UN regulation 155 cyber security are being enforced to tighten security.
For keyless automotive entry systems, the way forward is to address implementation and design issues with application security testing, said Dr Oka. Vulnerabilities such as improper signature verification (in the case on the key fob), could have been detected using static code analysis, software composition analysis (to identify known vulnerabilities), and fuzz testing (to detect unknown vulnerabilities). Additionally, it may be possible to detect these types of issues during penetration testing, focusing on high-risk areas such as security-related functions and firmware updates.
For the second weakness found in the missing certificate verification in the design of the pairing protocol between the BCM and the key fob, security design reviews are prescribed. Moreover, said Dr Oka, “it is imperative to perform a proper threat analysis and risk assessment of the target system to identify high-risk areas, which helps define appropriate security requirements and assists in designing suitable security controls. Additionally, it may be possible to detect these types of issues during penetration testing, focusing on high-risk areas such as security-related functions and pairing functions.”
While it is not realistic to expect 100% secure automotive systems, we should and can expect automotive firms to deploy appropriate measures for enabling firmware updates to patch newly-detected vulnerabilities. “Such firms need to establish internal processes and workflows to monitor, gather, and process vulnerability information, such as what is provided by security researchers, in order to respond accordingly,” Dr Oka concluded.
Accordingly, when the vulnerabilities were disclosed to Tesla in August 2020 by security researchers, the firm released an over-the-air (OTA) patch in November 2020. Have you checked with your car’s manufacturer about such updates yet?
(Note: Since there is limited information publicly available, please note also that some assumptions have been made about the target systems and type of weaknesses/vulnerabilities in order to facilitate this discussion on security solutions.)





















