In a battle of wits and speed, pentest attackers can triumph over human defenders unless an AI nemesis is the gatekeeper …
From North Korean hackers targeting a nuclear power plant in India to ransomware shutting down operations at a US gas facility, and across Honda’s manufacturing sites, 2020 has been the year of attacks on critical operational technology (OT) infrastructures.
Digital transformation has caused Industrial Control Systems (ICS) to converge with traditional IT networks. Consequentially, the number of cyberattacks that start in the corporate network before spreading to operational technology has increased dramatically.
Recently, a state-of-the-art attack was simulated at an international airport. The ‘attacker’ had performed reconnaissance and made lateral movements in the system. In addition to vulnerability scanning, protocol fuzzing was use: the latter is a technique in which the attacker sent nonsensical commands over an ICS communication channel in order to confuse the target device, causing it to fail or reboot.
Lurking and pouncing
The attack spanned multiple days and targeted the Building Management System (BMS) and the Baggage Reclaim network, with attackers utilizing two common ICS protocols (BacNet and S7Comm) and leveraging legitimate tools (such as ICS reprogramming commands and connections through SMB service pipes) to evade traditional, signature-based security tools.
Due to the patient and systematic method of lurking, reconnaissance and evasion, the attack was designed to succeed. Had the attack been real and had it been successful, the attackers (potentially activist groups, terrorist organizations, and organized criminals) could have caused significant operational disruption (or even worse) to the airport.
For example, the BMS that was managing temperature settings, sprinkler systems, fire alarms, fire exits, lighting, and doors in and out of secure access areas could have permitted physical intrusions and thereby additional harm to people and infrastructure on top of cybersecurity. Access to baggage reclaim networks can be used by criminals seeking to smuggle illegal goods or steal valuable cargo.
This simulation showcases the possibilities for an advanced cybercriminal or state-sponsored threat actors looking to compromise integrated IT and OT networks. The majority of leading ICS ‘security’ vendors are signature-based, and may fail to pick up on novel techniques and utilization of common protocols to pursue malicious ends. This is exactly how ICS attacks have continued to hit the headlines this year.
Defending ICS with AI
According to David Masson, Director of Enterprise Security, Darktrace, AI-powered anomaly detection solutions are effective in detecting every stage of sophisticated ICS attacks, even without reference to any list of known exploits, company assets, or firmware versions.
Any unusual attempts to read or reprogram single coils, objects, or other data blocks will be logged by AI algorithms and autonomous measures executed while personnel are alerted.
Masson elaborated on how stealthy and evasive a sophisticated attack can be. In this case, at the first stage of the attack, a new device was introduced to the network, using ARP spoofing to evade detection from traditional security tools.
The attacker then scanned a target device and attempted to brute-force open services. Once the target device had been hijacked, the attacker then sought to establish an external connection to the Internet. External connections should not be possible in ICS networks, but attackers often seek to bypass firewalls and network segregation rules in order to create a command and control (C2) channel.
The hijacked device then began performing ICS reconnaissance using Discover and Read commands. Unusual BacNet and Siemens S7Comm protocol commands targeting the ICS device as part of this reconnaissance were already detected by AI then.
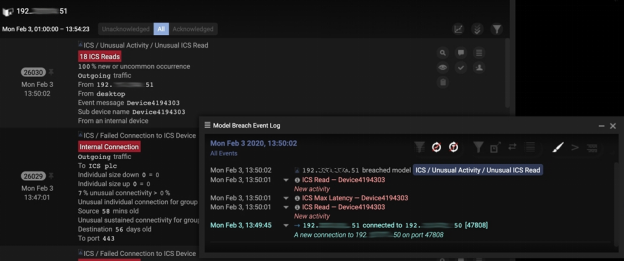
Next, the attacker enumerated through multiple ICS devices in order to perform lateral movement throughout the ICS system. Once they had learned device settings and configurations, they used ICS Reprogram and Write commands to reconfigure machines. The attacker attempted to use known vulnerabilities to exploit the target devices, such as the use of SMB, SMBv1, HTTP, RDP, and ICS protocol fuzzing.
The attacker took deliberate actions to evade the airport’s cyber security stack, including making connections using ICS protocols commonly-used on the network for devices. While non-intuitive security tools would have failed to pick up on this activity, the AI cybersecurity system’s deep packet inspection was able to identify unusual commands used by the attacker within those ‘normal’ connections.
Bridging human cyberskills gaps
Finally, the attacker used ARP spoofing to slow any investigation using asset management-based security tools—including two other solutions being trialed by the airport at the time of the simulated attack. The ‘threat actors’ also used multiple devices throughout the intrusion to throw defense teams off the scent trail.
However, the autonomous AI technology had already launched an automated investigation into the incident. The defense system identified all of the attack devices and produced summary reports for each, showcasing the ability to not only save crucial time for security teams, but bridge the skills gap between IT teams and ICS engineers that could have led to insufficient crisis decisions.
The AI deep learning software had immediately begun investigating after the first model breach, and was continuing to stitch together disparate events across the network to produce a natural language summary of the incident, including recommendations for action to administrators.
The incident showcases the extent of Cyber AI’s detections in a real-world ICS environment, and the level of detail a cyber-AI defense solution can provide following an attack.
As Industrial Control Systems become increasingly integrated with the wider IT network, the importance of securing these critical systems cannot be understated, said Masson.