Here is a blow-by-blow description of how state-sponsored threat actors execute such evasive, persistent espionage and surveillance campaigns.
Ever wondered how the really high-level hush-hush cyberattacks take place at government levels?
We have seen in spy movies how cyberattacks are perpetrated by state-sponsored threat actors, moles, sleeper cells and double agents. In real life, the day-to-day espionage operations detected by national spy agencies are often too sensitive to be divulged.
That is why the following account of one multi-stage espionage campaign is worth a read. Rest assured that all the sensitive details have been redacted: the cyber-forensic information you will receive, courtesy of the threat researchers at Trellix, is now cleared for public disclosure.
One day in early Oct 2021
It has been established that preliminary work for breaching an unspecified government installation had already taken place in June 2021, when malicious domains were registered in preparation for attack.
In early October, a six-stage attack targeting high-ranking government officials overseeing national security policy, as well as individuals in the defense industry, was launched.

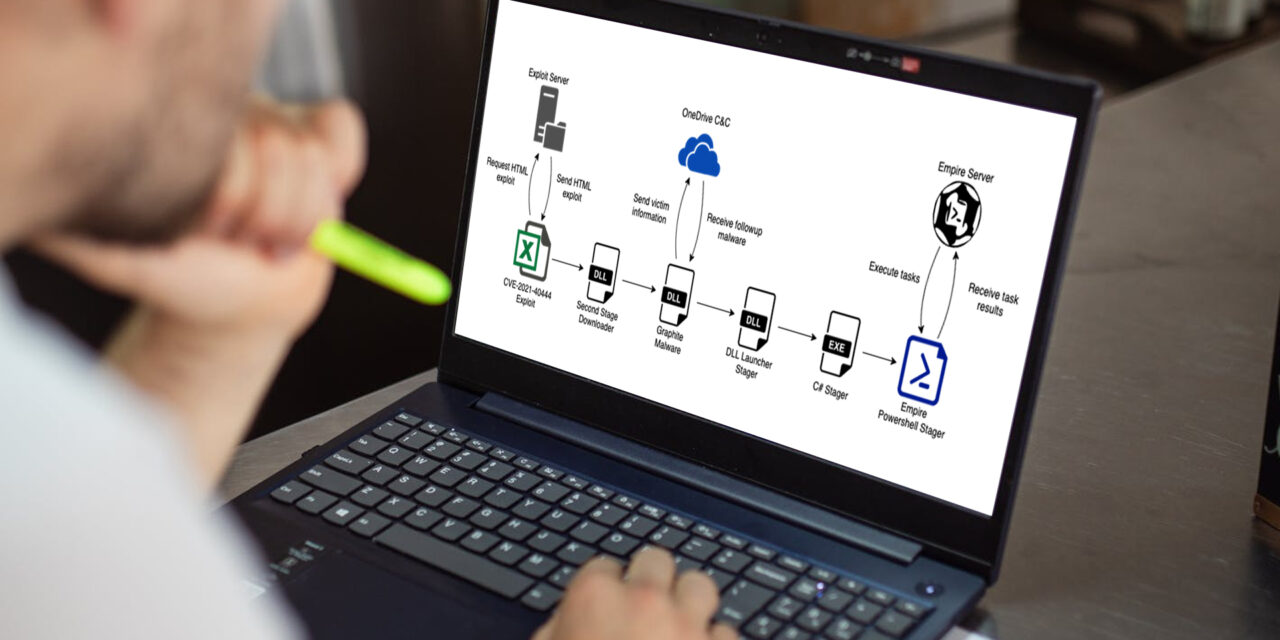
Here are the details of what took place in the six stages:
- The first stage started with the execution of an Excel downloader, most likely sent to the targeted government officials via a spear phishing email. The downloader exploited an MSHTML remote code execution vulnerability (CVE-2021-40444) to execute a malicious executable in memory.
- This stage involved a DLL executable, fontsubc.dll, resulting from a successful Stage 1. This file exported a function called CPlApplet that Windows recognizes as a control panel application. Primarily, this acted as a downloader for the next-stage malware located at websites set up way back in June and July. Ultimately, the downloaded malware was decrypted and the payload launched—except if file integrity checks failed.
- The third stage also involved a DLL executable dfsvc.dll, never written to disk, named Graphite due to the use of the Microsoft Graph API to use OneDrive for C2. It is very likely that the developers of Graphite used the Empire OneDrive Stager as a reference due to the similarities of the functionality and the file structure used in the OneDrive account of the actors. This stage is where reconnaissance data of the compromised machine’s running processes and other important data were uploaded into the hackers’ OneDrive account.
The Graphite malware also established a way to download further executable code from specific websites, check the integrity of the code and execute the payloads as needed.
This stage of the attack used Microsoft’s Graph API to leverage OneDrive as a C2 server—a technique not seen by Trellix researchers before. - Here, a DLL file named csiresources.dll was embedded into a Graphite shellcode task used to reflectively load the executable into the memory of the process and execute it. The malware tried to find the file EhStorShell.dll in the System32 folder and load it. With this, the malware made sure that the original EhStorShell.dll file was loaded into the explorer.exe context. This step paved the way for achieving persistent in the victim’s system in a follow-up phase involving the COM Hijacking technique.
Next, the malware loaded, initialized and started the .NET CLR Runtime, decrypted the .NET next-stage payload and loaded it into memory. Lastly, it executed the file using the .NET Runtime. - Now, a .NET executable named Service.exe that was embedded and encrypted in the previous stage is launched. Its main goal was to create an instance of a PowerShell object, decrypt the embedded PowerShell script using XOR operations, and decode it with Base64 before finally executing the payload with the Invoke function. The reason behind using a .NET executable to load and execute PowerShell code is to bypass security measures like AMSI, allowing execution from a process that should not allow it.
- Finally, the last stage was a PowerShell script, specifically an Empire HTTP Stager, which was embedded and encrypted in the previous stage. The main functionality of the script was to ‘call home’ to the pre-registered hacker websites to send the initial information about the system and download the encrypted Empire agent, decrypt it with AES-256 and execute it.
Final outcome: highly-sensitive information from as high up as a country’s Prime Minister’s Office was compromised covertly over the period from Oct to Nov 2021. Other victims included government officials and personnel in the defense industry.
Attributions and intentions
During the timeline of this espionage operation there were some political tensions around the Armenian and Azerbaijani border. Therefore, from a classic intelligence operation point of view, it made complete sense for state-sponsored threat groups to infiltrate and gather information to assess the risk and movements of the different parties involved.
A number of the attack indicators and apparent geopolitical objectives resembled those associated with a previously uncovered threat actor APT28. While researchers cannot attribute any campaign solely based on such evidence, they have a moderate level of confidence that the assumption is accurate.
Note the innovative use of the OneDrive service for C2 services through querying the Microsoft Graph API with a hardcoded token in the malware. This type of communication allowed the malware to go unnoticed in the victims’ systems since it only connected to legitimate Microsoft domains and did not produce any suspicious network traffic.
The forensic evidence point to very skilled threat actors based on how infrastructure, malware coding and operations were set up.